DDoS Threat Intelligence Map from A10

Data is not a defense. You need actionable intelligence.
Security researchers are swamped with massive volumes of data created during attempted attacks every day. But raw data cannot be used to develop an actionable defense until it is put into context and transformed into useful intelligence.
Threat intelligence combines the information acquired from the repeated use of attacking agents with the knowledge gleaned from millions of vulnerable IP addresses and hosts. Security researchers use this intelligence to proactively improve DDoS defenses.
Maps of the past are no help. This map shows the future.
A10 has created the DDoS Threat Intelligence Map to help you visualize the DDoS threat landscape and prepare for the next wave of DDoS attacks against your infrastructure.
Unlike the attack maps already on the internet that only show attacks that have already happened, A10’s DDoS map give you insights into where the next DDoS attacks will come from. By combining this knowledge with A10’s actionable DDoS threat intelligence platform, Thunder TPS, you can take a proactive approach to DDoS protection.
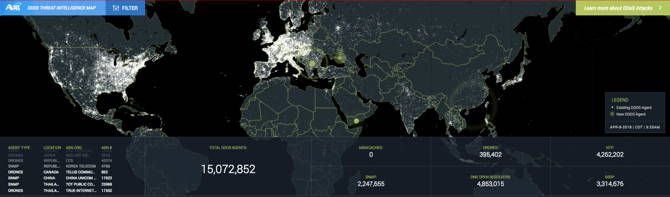
A10’s DDoS Threat Intelligence Map
What can you learn from the DDoS Threat Intelligence Map?
We all wish we could predict the future, but you may not know why or when a DDoS attack is going to come. You just know that it will come. By knowing where the weapons are, you can build a more effective defense. A10’s DDoS Threat Intelligence service, powered by A10 Research and ThreatSTOP, identifies millions of IP addresses commonly used as agents for DDoS attacks.
Unlike legacy DDoS defenses that only support thousands of blacklist entries, A10’s map includes large class-lists of threat objects with millions of entries that can be dynamically updated to make threat intelligence proactively actionable. This threat intelligence includes IP addresses of reflection attack agents, sprawling IoT botnets, and DDoS botnets actively used in the last 24 hours.
You can choose the categories of attack agents that you want to view, such as DNS or drone agents, see the geolocation of potential attacking elements, and check out entries that have been newly identified or deprecated from the snapshot of the near real-time DDoS threat feed.
How to navigate the A10 DDoS Threat Intelligence Map
White dots show the geolocation of an identified potential DDoS threat agent | Green pings show new threat agents that have been identified and added to the threat feed. | Blue pings show threat agents that has been removed from the threat feed. |
- Drones are identified DDoS malware infected hosts
- Abuse are hosts who are identified performing malicious activity, including but not limited to DDoS attacks, scanning and malware delivery
- DNS Open Resolvers are publicly exposed Domain Name System servers that respond to unauthenticated requests and are vulnerable to exploitation in an amplification attack
- NTP are publicly exposed Network Time Protocol servers that respond to unauthenticated requests and are vulnerable to exploitation in an amplification attack
- SSDP are publicly exposed Simple Service Discovery Protocol servers that respond to unauthenticated requests and are vulnerable to exploitation in an amplification attack
- SNMP are publicly exposed Simple Network Management Protocol servers that respond to unauthenticated requests and are vulnerable to exploitation in an amplification attack
- TFTP are publicly exposed Trivial File Transfer Protocol servers that responds to unauthenticated request and is vulnerable to be exploited in an amplification attack
- COAP is a publicly exposed host with Constrained Application Protocol active, that responds to unauthenticated requests and is vulnerable to be exploited in an amplification attacks
- Memcached shows publicly exposed memory objects caching servers that respond to unauthenticated requests and are vulnerable to exploitation in an amplification attack
- CLDAP are publicly exposed Connection-less Lightweight Directory Access Protocol server, that responds to unauthenticated requests and is vulnerable to be exploited in an amplification attack
- CHARGEN are publicly exposed Character Generator Protocol server, that responds to unauthenticated requests and is vulnerable to be exploited in an amplification attack
- ASN # are officially registered autonomous system numbers
- ASN ORG are the owners of the ASN where threat entries reside
DDoS Threat Intelligence from A10 Networks
Our Thunder TPS products include a DDoS Threat Intelligence service updated in real-time. Other companies offer lists of just tens of thousands of DDoS agents. The A10 DDoS Threat Intelligence includes a Class List of nearly 100 million known objects. The list includes the malicious objects you see in the A10 DDoS Threat Intelligence map, and more. First Thunder TPS will blacklist these DDoS weapons.
More than just the threats, A10’s DDoS Threat Intelligence includes tens of millions of trusted objects to whitelist. This prevents false positives that will interupt your legitimate traffic. Protect your organization from DDoS threats with the largest list of DDoS attack weapons. Thunder TPS gives you surgical precision of DDoS protection far beyond any other DDoS attack systems on the market.
Find out how you can protect your organization from DDoS attacks with A10’s DDoS Threat Intelligence service.
Learn more about A10’s DDoS protection with Thunder TPS
- Effective Service Provider DDoS Protection That Saves Dollars And Makes Sense
- DDoS Defense Monitoring and Management
- A10 DDoS Protection Cloud
- Ensure Enterprise DDoS Resilience
- DDoS Destruction: Defending Online Gaming Networks