Executive Order for Cyber-Attack Prevention Promotes Zero Trust Architecture

After every election of the federal government, the new administration faces the same challenge: How to maintain and repair critical national infrastructure.
Every administration inherits infrastructure built by previous administrations but rarely has that infrastructure been adequately funded for future maintenance. This is why, according to an analysis of the U.S. Department of Transport 2020 National Bridge Inventory (NBI) database by the American Road & Transportation Builders Association (ARTBA), there are more than 220,000 U.S. bridges—some 36 percent of the total number—in need of major repair work or complete replacement. At the current pace that bridges are being refurbished or replaced, ARBTA predicts it will take 40 years to repair the backlog of structurally deficient, that is, dangerous, bridges.
As urgent as the problem of the aging bridge infrastructure is, there’s a more recent infrastructure threat that is finally getting some serious attention: The cyber security infrastructures that protect computer networks run by both the federal government and the private sector.
Unlike U.S. bridges built over the span of a couple of centuries, these networks were built over just a few decades of intense innovation and have become just as critical, arguably even more so, to the functioning of the country as bridges are.
This digital infrastructure effectively underpins the running of the country and every time the cyber-attack prevention measures fail, there’s the threat of major disruptions in everything from the power grid, healthcare, and fuel supplies, to government agencies including the military and even the U.S. election system.
To address this problem, on May 12, 2021, President Biden signed an executive order to:
… improve the nation’s cybersecurity and protect federal government networks. Recent cybersecurity incidents such as SolarWinds, Microsoft Exchange, and the Colonial Pipeline incident are a sobering reminder that U.S. public and private sector entities increasingly face sophisticated malicious cyber activity from both nation-state actors and cyber criminals. These incidents share commonalities, including insufficient cybersecurity defenses that leave public and private sector entities more vulnerable to incidents.
The order is ambitious and outlines seven goals:
- Remove barriers to threat information sharing between government and the private sector
- Modernize and implement stronger cybersecurity standards in the federal government
- Improve software supply chain security
- Establish a cybersecurity safety review board
- Create a standard playbook for responding to cyber incidents
- Improve detection of cybersecurity incidents on federal government networks
- Improve investigative and remediation capabilities
Threat Information Sharing
Many organizations have been hesitant or downright unwilling to share breach information. Sometimes contractual obligations are responsible for this hesitancy but more often it comes down to companies being unwilling to damage their image and reputation by admitting that their systems were compromised.
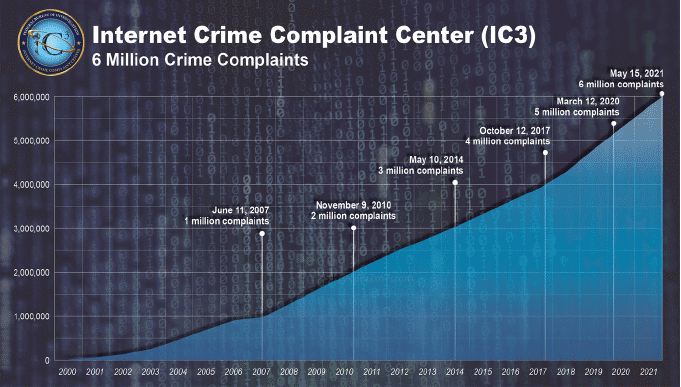
It took nearly seven years for the FBI’s Internet Crime Complaint Center (IC3) to log its first million complaints. It took only 14 months to add the most recent million
Under the European Union’s General Data Protection Regulation (GDPR) organizations are required under the threat of significant penalties to report data breaches, but in other jurisdictions such as the U.S., the laws are far less stringent. In the U.S., there are similar provisions under, for example, the Health Insurance Portability and Accountability Act of 1996 (HIPAA) but there have been few laws to report other cyber security-related crimes to law enforcement. Even though the FBI’s Internet Crime Complaint Center (IC3) received its 6 millionth incident report in May 2021, it’s estimated that cybercrimes are significantly under-reported.
The executive order states that:
Removing any contractual barriers and requiring providers to share breach information that could impact Government networks is necessary to enable more effective defenses of Federal departments, and to improve the Nation’s cybersecurity as a whole.
Federal Government Cyber Security Standards
This is a key section of the executive order because it mandates three key cyber-attack prevention requirements:
Outdated security models and unencrypted data have led to compromises of systems in the public and private sectors. The Federal government must lead the way and increase its adoption of security best practices, including by employing a zero-trust security model, accelerating movement to secure cloud services, and consistently deploying foundational security tools such as multifactor authentication and encryption.
The promotion of the Zero Trust architecture is arguably one of the biggest advances in federal cyber security infrastructure defense and cyber-attack prevention thinking.
Supply Chain Security
Over the course of the novel coronavirus pandemic we’ve seen how supply chain disruption causes a whole range of problems limiting the availability of everything from eggs, bathroom tissue, and garden gnomes to personal protective equipment (PPE) for healthcare workers. The executive order will:
… improve the security of software by establishing baseline security standards for development of software sold to the government, including requiring developers to maintain greater visibility into their software and making security data publicly available … This is a long-standing, well-known problem, but for too long we have kicked the can down the road. We need to use the purchasing power of the Federal Government to drive the market to build security into all software from the ground up.
Cyber Security Safety Review Board
Modeled after the National Transportation Safety Board (NTSB), the proposed Cyber Security Safety Review Board:
… co-chaired by government and private sector leads, that may convene following a significant cyber incident to analyze what happened and make concrete recommendations for improving cyber security.
Cyber Incidents Response Standard Playbook
The establishment of a standard playbook for federal departments and agencies will “ensure all Federal agencies meet a certain threshold and are prepared to take uniform steps to identify and mitigate a threat. The playbook will also provide the private sector with a template for its response efforts.”
Federal Government Networks Cybersecurity Incident Detection
The heart of this goal is to speed up the deployment of “foundational cyber security tools and practices” and central to this is “enabling a government-wide endpoint detection and response system and improved information sharing within the Federal government.”
Improve Investigative and Remediation Capabilities
The goal of mandated cyber security event logging for federal departments and agencies is to improve intrusion detection, speed up mitigation, and make it easier to determine the impact of an incident.
So, What’s Missing?
The realization of the executive order goals will be significant steps forward in hardening federal and private infrastructure and supporting national cyber-attack prevention but the most significant requirement of the order is the use of the Zero Trust architecture. That said, something is missing: Centralized and dedicated SSL inspection.
Without SSL inspection, the Zero Trust architecture is unable to do what it was designed to do – protect networks. SSL inspection provides in-depth traffic examination and:
- Detection and amelioration of malicious requests
- Monitoring data entering and leaving networks for analytics
- Enabling better access management
- Protecting against DDoS attacks
- Enabling efficient white- and black-listing of users and IP addresses
- Ensuring uniform access and data transfer policies
President Biden’s executive order is the most far-reaching cyber security infrastructure and cyber-attack prevention strategy the federal government has ever put forward and its promotion of the Zero Trust architecture is the only practical and effective foundation for all of its goals. Adding SSL inspection completes the architecture and ensures, unlike our bridges, that our cyber security and cyber-attack prevention foundations are future-proofed.
Other Articles and Assets of Interest
- The Implications of the SolarWinds Cyberattack
- 2020 Was a Busy Year for DDoS Attacks
- Driving Digital Transformation with Effective Application Delivery and Security
- How to Defeat Emotet Malware with SSL Interception
- Zero Trust is Incomplete Without TLS Decryption
- Is Your Enterprise Perimeter Equipped To Defend You From Modern Cyber Attacks?
- Bring Visibility to the Blind Spot with A10 Networks & Fidelis Cybersecurity
How A10 Can Help
A10 Networks Thunder® SSL Insight fulfills the promise of the Zero Trust architecture by delivering full traffic visibility through SSL inspection. By taking a “decrypt once, inspect many times” approach, the A10 SSL inspection solution lets the cyber security infrastructure rapidly inspect all traffic in clear text to avoid performance penalties and excess complexity.