Curing Healthcare Cyber Security – A Better Way To Protect Patient Data

The Hippocratic Oath commands doctors to “first, do no harm.” Healthcare professionals have a proud tradition of honoring this commitment to their patients—but in today’s data-centric world, they face an equal obligation to secure the Protected Health Information (PHI), Personally Identifiable Information (PII), and financial data of their patients as well. And ironically, one of the most common “security” measures healthcare organizations take to strengthen cybersecurity, i.e., encryption of data on the go, can actually make patient data more vulnerable to attacks. By using encryption to protect communications, they make it impossible for firewalls and other security devices to detect malicious traffic and files hiding within legitimate traffic. Decryption for TLS/SSL inspection could be a viable approach, but it has typically brought high penalties in cost, scalability, and performance. So, what are medical centers, insurance providers, billing services companies, and other healthcare organizations going to do?
To fulfill their responsibility to patients, it is first of all, essential for healthcare industry organizations to understand that encryption provides privacy but not security—and it can even undermine security in some ways. To avoid creating more problems than solutions, they must find a way to leverage encryption without undermining the effectiveness of the rest of their security stack.
The Risks Facing Patient Data and the Organizations Holding It
The nature of healthcare makes cybersecurity a critical challenge for practitioners and supporting organizations. With vast amounts of PHI, PII, and financial data, they are rich targets for attacks such as ransomware and data theft. They also face stringent data compliance regulations, which adds to the importance of effective data protection. There are endless ways for something to go wrong, from a mistake by a well-intentioned employee, or sabotage by a malicious insider, to an outright attack via phishing or trojan-based malware by hackers seeking sensitive data for illicit sale or exploitation.
The impact of a breach can be devastating. The notorious WannaCry ransomware attacks of 2017 hit targets in 150 countries worldwide. Among its victims was the U.K.’s National Health Service, forcing the cancellation of more than 19,000 appointments at a cost of £20 million ($25 million), and necessitating system repair and upgrades costing an additional £72 million ($90 million). In February 2015, a breach of Anthem, Inc. affected nearly 80 million people and brought a record-setting $16 million fine from the Department of Health and Human Services’ Office for Civil Rights (OCR), as well as a civil settlement of $115 million.
Compliance Commands Vigilance
Since 1996, the U.S. Health Insurance Portability and Accountability Act (HIPAA) has imposed strict requirements for the protection of health information held or transferred in electronic form. Penalties for violations can be severe, including fines of up to $1.5 million per violation category, per year. In the past year alone, Cottage Health paid $3 million to settle a case of potential HIPAA non-compliance; Touchstone Medical Imaging paid $3 million following a breach exposing the PHI of over 300,000 patients; and Jackson Health System paid over $2.15 million in civil penalties for a series of HIPAA violations.
$3.9 million is the total impact with an average cost of $150 per record lost for the average breach
The newly introduced GDPR rule now poses similar risks in the E.U. Already last July, the E.U. fined British Airways £183 million ($228 million) for leaking the personal data of 500,000 customers. It’s only a matter of time until companies holding healthcare-related data find themselves in the same position. And cost aside, reputational damage can have long-lasting implications for an organization’s profitability, growth, and even viability following a high-profile cybersecurity failure.
The Problems with Encryption and Decryption
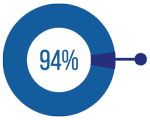
Most organizations today rely on encryption to protect internet communications; according to the Google Transparency Report, over 90 percent of the traffic received by the company and its products is encrypted via SSL (Secure Sockets Layer) or TLS (Transport Layer Security) connections. The same can be said for other browsers. Healthcare organizations are no exception to this trend—and neither are hackers. In fact, more than half of the malware attacks seen today are using some form of encryption for establishing communications or infiltrating systems.
94% of Internet traffic is encrypted via SSL or TLS connections according to the Google Transparency Report
While encryption can seem like a simple and inexpensive way to avert spoofing, man-in-the-middle attacks, and other common exploits, it presents problems at each stage of the typical attack. As a hacker tries to penetrate network defenses, encryption renders malware invisible to the organization’s security infrastructure, including advanced threat protection (ATP) systems, intrusion detection systems (IDS), intrusion prevention systems (IPS), firewalls, antivirus software, and secure web gateways. When the malware seeks to establish a connection to command and control servers, encryption makes it impossible to track or stop these communications. And as the malware starts smuggling out targeted files, encryption once again blinds traditional data loss prevention (DLP) devices and forensic devices. Simply put, encryption can leave the rest of the security stack useless for stopping an attack.
One theoretical solution would be to decrypt incoming traffic to allow inspection, a capability offered by the latest next-generation firewalls (NGFW) and intrusion prevention systems. In reality, this usually proves less than practical. A test conducted by NSS Labs found an average of a 60 percent performance degradation when decryption is enabled in an NGFW. Compensating for this loss would call for scaling up these security devices on a regular basis to meet the needs of the network. However, these additional devices, and others in the security infrastructure, only add further latency, create network bottlenecks, and increase the operational costs and complexity of the network. Repeat this scenario across the rest of the security stack, including DLP, antivirus, firewall, IPS, and IDS systems needing their own decryption capability, and the resulting scalability issues, costs, bottlenecks, and failure points underscore the issues with this approach.
Moreover, a distributed decryption strategy, as outlined above, can also lead to multiple points of failure in the network, as the essential private keys and certificates would have to be dispersed across multiple security devices in order to help them intercept, decrypt, and re-encrypt the traffic.
A Better Way to Ensure Privacy and Security
The crux of the problem isn’t encryption and decryption as such; it’s the way these technologies have been implemented. By taking a different approach, organizations can continue to make effective use of encryption without compromising the rest of their security investments. The solution: to shift focus from slow, inefficient, and costly device-by-device decryption, to centralized decryption on a single dedicated solution. This makes it possible to decrypt traffic once for inspection by separate security devices across the stack in tandem, and then re-encrypt it once afterwards.
With this model, organizations can eliminate the encryption blind spot to detect data breaches and cyberattacks. In addition to strengthening security, organizations can then enforce and ensure compliance with data privacy and protection standards such as GDPR and HIPAA—key requirements for every healthcare organization.
This approach can now be fully implemented with the A10 Networks Thunder ® SSL Insight solution, which provides complete visibility into encrypted traffic for other security solutions while sparing them the CPU-intensive SSL/TLS operations that can impair performance and scalability. A central point of decryption ensures peak performance and eliminates decryption overhead for devices throughout the security infrastructure, while a single pane of glass simplifies visibility, management, and analysis.