Microsoft Office 365 Enterprise Network Architecture
This article presents a high-level overview of the Office 365 network infrastructure from end-user clients to the services running inside the Microsoft clouds. This is a cloud-based software are a service (SaaS) solution and requires specific architectural planning for enterprise network architectures.
This topic is broad and complex. It is covered briefly here as an introduction and a starting point, and this article provides links to specific topics for further research.
Additional articles on Office 365 enterprise architectures:
Network Design for Scale and Performance
Background
Office 365 is a SaaS solution that was traditionally designed to be hosted in company local datacenters with strong security perimeters. Locally-installed services have different network requirements and use LAN resources. Cloud-hosted services use a WAN and internet networks.
SaaS services require fundamentally different network architectures:
- Increased usage and reliance on WAN resources since documents and data are accessed and stored on public cloud resources
- Greatly-expanded performance requirements for edge network and security devices. Edge security is complex and resource-intensive requiring traffic inspection and analysis.
- Multiple long-lived active TCP sessions expand the resources of edge systems to buffer and process open sessions.
Office 365 as a SaaS combines dozens of SaaS products, which open multiple TCP sessions per application for each user. Enterprise IT network architectures can benefit from this combined service architecture since all of the Office 365 services can be managed and optimized with a single architectural design.
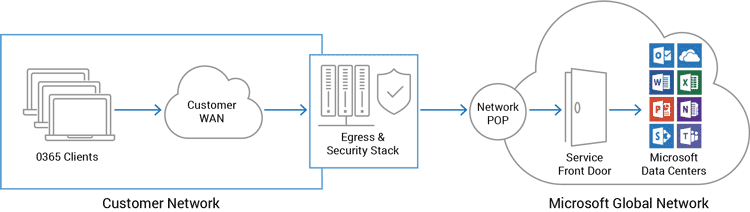
The architectural diagram above depicts the customer network infrastructure with clients accessing Office 365 services. Traffic is protected by a stack of network and security systems at the customer egress edge. Customer networks then route traffic to the Microsoft network point of presence (POP) so it can be intelligently routed to the Office 365 Service Front Door.
Enterprise edge systems can add advantages by designing the network architecture to:
- Route non-Office 365 traffic to appropriate edge systems, reducing edge resource requirements
- Pass Office 365 traffic directly to the Microsoft Global Network, offloading SSL processing to Microsoft and increasing network performance
O365 Network IP Traffic
Network managers must be aware of network traffic details to manage access, performance and security.
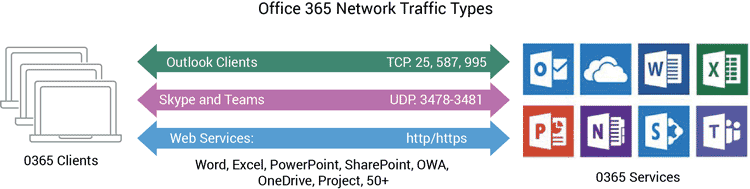
Most of the Office 365 services are accessed via HTTPS web protocols either with a web browser or with a local client (i.e., OneDrive).
Examples of services using HTTP/HTTPS:
- Outlook Web app (OWA)
- SharePoint Online
- OneDrive for Business
- Word, PowerPoint, Excel
Two exceptions are Outlook and Skype for Business.
- Outlook client (Exchange Online)
- SMTP (25, 587)
- POP3 (995)
- Various Outlook add-ons
- Skype for Business Online and Teams
- UDP 3478-3481
Network routing and security access must be supported for Outlook (Exchange Online), as well as UDP support for Skype for Business.
O365 Microsoft Global Network
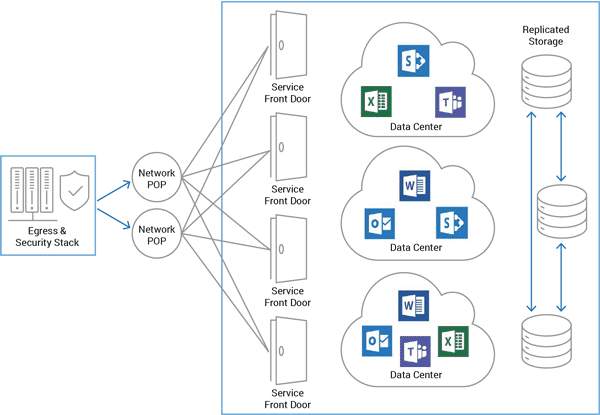
Office 365 services are accessed by the Microsoft Global Network, which is a global wide-area network providing cloud services to Azure and other Microsoft services. This is comprised of a large and growing set of datacenters, servers, content distribution networks and edge-computing systems connected by one of the world’s largest network infrastructures.
Microsoft Office 365 services are not only distributed over multiple datacenters residing within the Microsoft Global Network but also replicated to other datacenters for reliability.
Note: The Microsoft Global Network contains 2500+ Networks, 150+ ISP Peers, 35+ datacenters
Customer traffic is routed by the Office 365 Service Front Door servers to the appropriate systems that are providing the specific services.
Routing to Office 365 Access Points
Microsoft is adding an ever-increasing number of network entry points closer to customer locations. Once on the Microsoft network, traffic is intelligently routed through the high-speed Microsoft Global Network.
To provide the best performance for Office 365 services, customers should connect to the nearest Microsoft network POP. Reducing the network path from the customer to the Microsoft network increases performance and reduces network latency.
For this to work correctly, the customer DNS servers should be located geographically close to the customer networks. Office 365 services use GeoDNS lookup and other technologies to determine where DNS requests are coming from and to redirect client traffic to the nearest geographically-located Service Front Door.
To locate the best Microsoft POP addresses, the local DNS servers should either:
- Best – be a local DNS server with root hints. This server will reside on the customer’s network and provide the exact customer network.
- Good – Forward to ISP DNS servers that reside on an ISP network segment residing on the same network segment as the customer network.
Corporate Egress Traffic
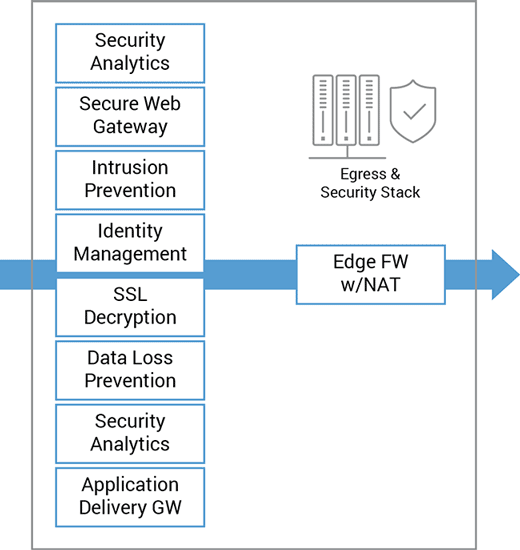
Office 365 traffic from clients traverse the edge network and security systems to reach the closet Office 365 cloud datacenter. This stack of edge systems is complex, expensive and must be highly reliable.
Office 365 services include end-to-end security services. Routing client traffic though the edge security stack can be redundant and can add increased delay and overhead. With this in mind, customers should bypass enterprise edge security systems and route directly to the Microsoft network.
Note: Microsoft recommends direct network connectivity to Office 365 services for faster and low-latency performance.
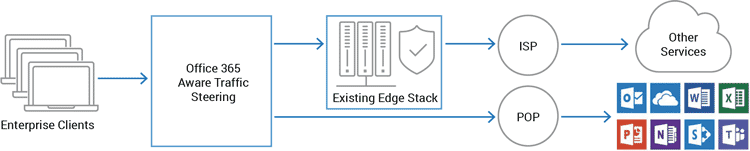
The benefits of steering Office 365 traffic directly to the Office 365 access point is it:
- Offloads traffic from the existing edge egress and security systems
- Expands the lifespan of the existing and expensive edge systems
- Increases Office 365 performance providing a better user experience
This network architecture is described in detail here: Design to Scale and Perform
Enterprise Branch Networks
Branch-office network architectures are often connected to central offices via VPN internet connections or expensive leased lines.
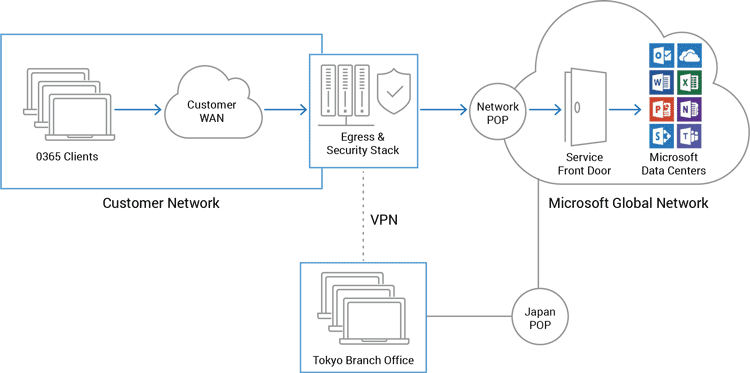
Branch-office networks can benefit by accessing Office 365 services directly instead of routing this traffic through the central office. This requires identifying Office 365 traffic and routing this traffic directly to a local Office 365 access POP.
The techniques for steering traffic and routing traffic to local Office 365 access points are the same as described above. This includes resolving Office 365 clients using a local DNS server.
References
- A10 ADFS and Office 365
- Office 365 Network Connectivity Principles
- Office 365 Client Connectivity
- Microsoft Skype for Business Online
- Managing Office 365 Endpoints
- NAT Support with Office 365
How A10 Networks Can Help?
A10 Networks has partnered with Microsoft to design an Office 365 solution for enterprise networks. The company’s Thunder® products provide a complete enterprise solution or can augment existing edge systems to offload, scale and secure Office 365 applications.
Benefits:
- Intelligent Office 365 traffic identification and steering
- Office 365 required capabilities such as HTTP header injection for tenant access control
- Traffic load balancing across multiple edge servers
- Advanced NAT capabilities
- SSL offload and packet inspection of SSL encrypted traffic