The Cost of a Data Breach and the Need for SSL Security
The cost of a data breach is soaring to unprecedented levels. According to IBM, the average cost of a data breach globally reached an all-time high of $4.35 million in 2022, a 12.7 percent increase from 2020. With sophisticated cyber criminals targeting the confidential data of organizations of all kinds—healthcare, financial services, government, technology, media, the list goes on—it’s never been more important to layer cybersecurity throughout the enterprise environment.
This includes addressing head-on the challenges of work from home cybersecurity through measures such as zero trust architecture and SSL security.In this blog, we’ll discuss the nature of the data breach threat, the factors driving the cost of a data breach, and cybersecurity tips to prevent data theft, ransomware, exfiltration of data, and other threats against an organization’s confidential data.
Data Theft, Data Exfiltration, and Other Types of Data Breaches
A data breach can come in many forms, from an inadvertent disclosure of data by a careless employee, or a hacker using compromised credentials to steal sensitive information, to a ransomware attack where a company’s confidential data is forcibly encrypted.
The type of data involved can vary widely as well, including personal health information (PHI) such as medical records, personally identifiable information (PII) such as birth dates and driver’s license numbers, financial data such as credit card and bank account numbers, intellectual property such as code or product designs, or trade secrets such as business strategy or customer lists. Whatever circumstances or motivations may be at play, any time an unauthorized individual views or takes a company’s data, a data breach has occurred.
Many data breaches involve the exfiltration of data. In this case, data is transferred from one system to another without consent, often beyond the corporate network. While this can be an honest mistake, it’s more often the act of a bad actor seeking to either sell the stolen data on the black market, or threaten to do so in order to extort a payment. Data exfiltration can also be combined with ransomware to increase the pressure on the victim to pay the ransom.
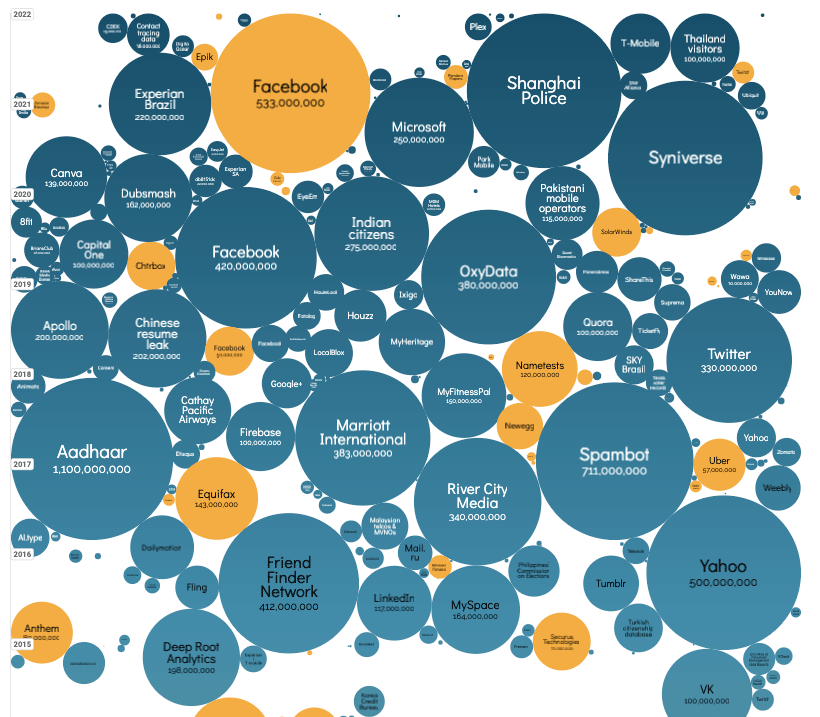
World’s biggest data breaches & hacks via Information is Beautiful
What Drives the Cost of a Data Breach—and What It Can Add Up To
A data breach of any kind can quickly trigger widespread and costly disruption within an organization. IBM factors four primary drivers into the cost of a data breach:
- Breach detection, investigation, and escalation, including crisis management
- Notification and communication with customers, regulators, and lawyers
- Business impacts such as downtime, dropped stock prices, and damage to the company’s reputation and customer relationships
- Post-breach expenses related to cybersecurity and payments for legal services, regulatory fines, and compensation
The company notes the challenges of work-from-home cybersecurity as a contributor to many breaches. While breaches come in many forms, they tend to have a similar financial impact, with phishing attacks, ransomware, and breaches through stolen or compromised credentials all resulting in between $4.5 million – $4.91 million in losses.
And costs can go much higher than IBM’s reported global average. In August 2021, T-Mobile disclosed an incident affecting more than 76 million of its customers. The following July, the company agreed in court to pay $350 million dollars to settle a class action lawsuit by its customers, and an additional $150 million to upgrade its data protection over the coming two years—an investment that, made earlier, might have averted the need for the customer settlement itself. Capital One faced a similar lawsuit following a 2019 data breach that affected 100 million customers, leading to a settlement of $190 million—in addition to the $80 million levied by the U.S. Office of the Comptroller of the Currency for the same incident.
As the notorious 2017 Equifax breach shows, the total cost of a data breach can have a long tail. In July 2019, the credit-monitoring company agreed to pay a settlement between $575 million – $700 million for its “failure to take reasonable steps to secure its network” against the exfiltration of data. The company had already been fined roughly $625,000 by the U.K. for the incident—an amount that would have been much higher under the E.U. General Data Protection Regulation (GDPR), which had not yet been adopted. Further penalties followed in 2020, including $7.75 million to U.S. financial institutions, $18.2 million to the state of Massachusetts, and $19.5 million to the state of Indiana. Adding injury to injury, Wall Street analysts pushed the company’s valuation $4 billion lower. The company ultimately reported $68.7 million in belated security costs in 2019.
Regulatory fines are a major contributor to the financial impact of data theft, data exfiltration, lax data protection, and other cybersecurity failures. For violations of the U.S. Health Insurance Portability and Accountability Act (HIPAA), which imposes strict requirements for the protection of health information held or transferred in electronic form, the Office for Civil Rights of the U.S. Department of Health & Human Services has received settlements or penalties totaling $133,519,272 since 2003. In 2021 alone, 38 companies were fined for General Data Protection Regulation (GDPR) data protection violations totaling 9.6 million euros. On the state level, Uber was fined $148 million in 2018 for failing to disclose a 2016 breach affecting 600,000 driver and 57 million user accounts.
In October 2022, Australian legislators raised the stakes further following a series of high-profile data breaches at Energy Australia, Telstra, G4S, Costa Group, MyDeal, and Dialog; the dark web release of sensitive personal medical information from a data theft against health insurer Medibank Private; and a breach at telecommunications giant Optus involving 10 million of its customers—or roughly 40 percent of the entire population of Australia. The newly passed Privacy Legislation Amendment (Enforcement and Other Measures) Bill 2022 penalizes companies allowing serious or repeated privacy breaches to the tune of $50 million or more.
Cybersecurity Tips to Protect Data with Zero Trust Architecture and SSL Security
As the threat of data theft continues to rise, a Zero Trust architecture has become a core tenet of modern cybersecurity. Based on principles including least privilege, the Zero Trust model seeks to limit data access permissions to the bare minimum required for each user’s job function. Continuous checks throughout the network help ensure that databases and other resources are accessed only by authenticated and authorized users and accounts. Network micro-segmentation and micro-perimeters, comprehensive visibility, analytics and automation, and well-integrated security solutions help complete the model.
However, Zero Trust architectures can be undermined by a common blind spot: SSL security. The vast majority of internet traffic today is encrypted to safeguard data and prevent spoofing, man-in-the-middle attacks, and other exploits. While encryption keeps data safe from the prying eyes of cyber criminals, though, it does the same for security devices—leaving them unable to detect malware, ransomware, or exfiltration of data in encrypted traffic. In fact, as many as 46 percent of malware attacks used encryption as part of their delivery and communication mechanisms in 2021. For this reason, a Zero Trust architecture must include SSL security technologies to decrypt inbound and outbound TLS / SSL traffic to allow SSL inspection by firewalls, intrusion prevent systems (IPS), data loss prevention (DLP), forensics, advanced threat prevention (ATP), and other security tools, then re-encrypt traffic to continue to its destination
How Can A10 Networks Help?
A10 Networks Thunder® SSLi helps organizations close the blind spot in a Zero Trust architecture by providing complete visibility into encrypted traffic to allow SSL inspection by other security solutions. Supporting SSL security through a highly efficient, centralized, dedicated decryption solution, Thunder SSLi performs decryption and encryption without adding latency, creating bottlenecks, or increasing the operational costs and complexity of the network.
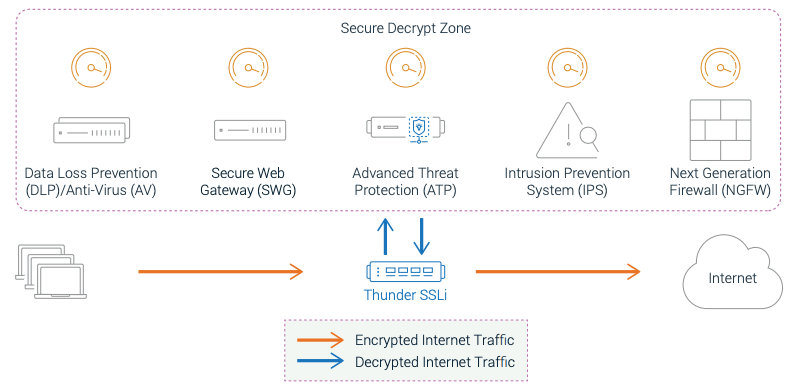
Thunder SSLi enables your existing security devices to inspect encrypted traffic with optimal performance, minimal latency, advanced analytics and maximizes your ROI.
Companies like T-Mobile and Equifax reported major investments in data protection only after a data theft or the exfiltration of data had occurred. Clearly, the time to strengthen cybersecurity is before such incidents occur—when it’s not too late to avoid regulatory fines, customer lawsuits, falling stock prices, and a corporate reputation tainted by carelessness with customer privacy.
Related Resources
- A Zero Trust Strategy for the Disappearing Perimeter (Webinar)
- Zero Trust and the New Normal for Cybersecurity (Webinar)
- Zero Trust is Incomplete Without TLS Decryption (White Paper)
- TLS, Compliance and Zero Trust – Protecting Users from Cyberattacks (Webinar)
- 5 Steps to Enhance Your Enterprise Security with High Performance SSL/TLS Decryption (eBook)