Centralized TLS Decryption: The Prerequisite to SASE, SSE, Zero Trust

Centralized TLS Decryption and the Elephant Inspection
When an organization embarks on the arduous journey of implementing reliable network security, its search often leads to confusing industry buzz words. If you and your organization are looking for frameworks, acronyms like Secure Access Service Edge (SASE), Security Service Edge (SSE), and Zero Trust security come to mind. If you’re looking for security solutions, acronyms like ADC, XDR, SD-WAN, and countless others come to mind. But hold your horses.
Whether it’s a framework or a solution you are looking to implement, there is a prerequisite that has yet to be satisfied. That is, how are you going to inspect and secure your traffic if there is no visible traffic to be inspected? Standard traffic nowadays is, by default, encrypted via the Transport Layer Security (TLS) protocol. In order to inspect the traffic, TLS decryption is required. Let’s take a quick trip down memory lane to explain how we arrived at this age of encryption/decryption. Afterwards, we’ll use an elephant analogy to simply describe how the A10 Thunder® SSL Insight (SSLi®) solution decrypts traffic to act as the precursor to a modernized security framework. Finally, as a deep dive, we have a case study examining a successful deployment of the Thunder SSLi solution.
The Wild West of Pre-encryption
Regardless of the security framework you subscribe to, whether Security Service Edge (SSE), Secure Access Service Edge (SASE), or the NSA-approved advocacy for Zero Trust security, every modernized security framework is heavily dependent on visibility. Originally, traffic was easily visible and vulnerable. As such, man-in-the-middle attacks, Heartbleed, POODLE, BEAST, CRIME, and other prevalent vulnerabilities could be exploited. Much like we wouldn’t want to display our SSN, birth certificates, and bank account information on our heads when we are walking down the street, a basic level of concealment for our sensitive data passing through the cyberspace was needed.
The Brief Respite of Encryption
This is where encryption technology comes in. Encryption really ramped up in 2018 when browsers made it mandatory for web traffic to be encrypted. Nowadays, more than 95 percent of all web traffic is encrypted. Unfortunately, encrypting traffic wasn’t the end all be all to realize sufficient security. Encrypted traffic prevents it from being tampered with and provides an outstanding baseline of security.
However, it could still carry malicious malware and malicious scripts within the packet. In laymen terms, when we deliver our mail, we stamp and seal our envelops, preventing them from being further tampered with. However, just because something is stamped and sealed in an official manner doesn’t mean that these official-looking envelopes always contain legitimate items. To ensure the legality of items within sealed envelopes, examination is required. Hence, the need for decryption technology quickly escalated. We had to do something about gaining visibility into these mystery locked boxes.
The Dystopic Reality of Post-encryption
Enter TLS decryption technologies. During the pre-encryption era, security devices could inspect the SSL/TLS traffic before forwarding it on.
With encryption becoming so popular, it is now necessary for these security devices to be able to decrypt the traffic before inspecting it. Most security devices to this day are still unable to perform TLS decryption, rendering these products ineffective. They can’t inspect something they can’t see. Some security vendors have begun advertising security devices that can leverage various forms of hardware acceleration to offload some of the decryption tasks. Unfortunately, while this may patch part of the problem, there exists a couple of larger problems.
Because TLS decryption is such a CPU-intensive task, security devices that are trying to decrypt, inspect, and encrypt all within one solution may end up experiencing a severe performance degradation. As a result of trying to natively perform TLS decryption, these security devices can become incapable of productively running TLS decryption or productively running inspection. From here, the solution would be to install decryption-capable inspection and security devices with redundancy, and to keep up with constant hardware refreshes. This solution comes with intense price hikes for the entire security solution required due to just the encryption upgrade requirements, but the alternative is for the organizations to skip TLS decryption altogether, thereby eradicating the utility of their security solutions, and increasing the overall threat attack surface.
Tying the Encryption Story Back to Zero-Trust Reality
So why is inspecting encrypted traffic tied to the big trends in network security? As an example, traffic inspection is critical to the aforementioned Zero Trust security model. This model, highly endorsed by the NSA, is a security strategy and framework that is also a key cornerstone in other security frameworks such as Gartner’s Secure Access Service Edge (SASE) and Security Service Edge (SSE).
Zero Trust security model is dependent on a “never trust, always verify” concept. In order to verify on a granular level, an enterprise is required to first possess full visibility of its traffic. Only from there can an organization enact granular policies based on ID, micro-perimeters, and other contextual information. In the new encryption-based reality, by default, traffic is not visible because all of it is transmitted through these encrypted black boxes. This is where A10 Networks comes in.
The solution: Secure Decrypt Zone Enables the Visibility Required for Zero Trust
Thunder SSL Insight is a dedicated and centralized decryption device that follows the “decrypt once, inspect multiple times” philosophy. Following successful decryption of the traffic, Thunder SSLi sends the packets off to a “secure decrypt zone” where many security devices can be deployed or service-chained to efficiently inspect the traffic as needed.
The Elephant Inspector Association: Modernized Decryption, Simplified
Let’s compare traffic that needs to be inspected to elephants passing through the Elephant Inspector Association (EIA). The legend below can be used as a reference to the different icons portrayed.

Traditionally, our Elephant Inspector Association only possesses the capacity to inspect green elephants, as we can see in figure 1.
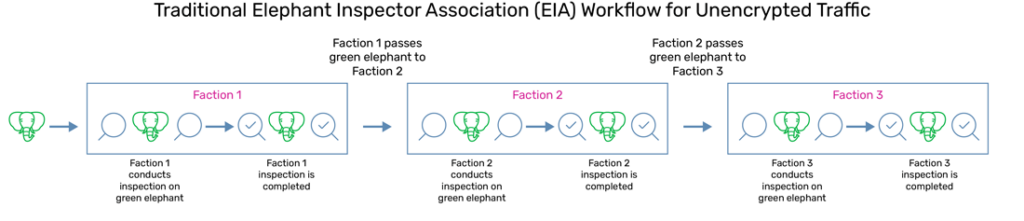
Fig 1: Elephant Inspector Association (EIA) Workflow for Unencrypted Traffic
If we came across a red elephant, we must transform said red elephant into a green elephant before it can be properly inspected by our Elephant Inspector Association, which consists of 20 factions. The traditional workflow can be seen in figure 2.
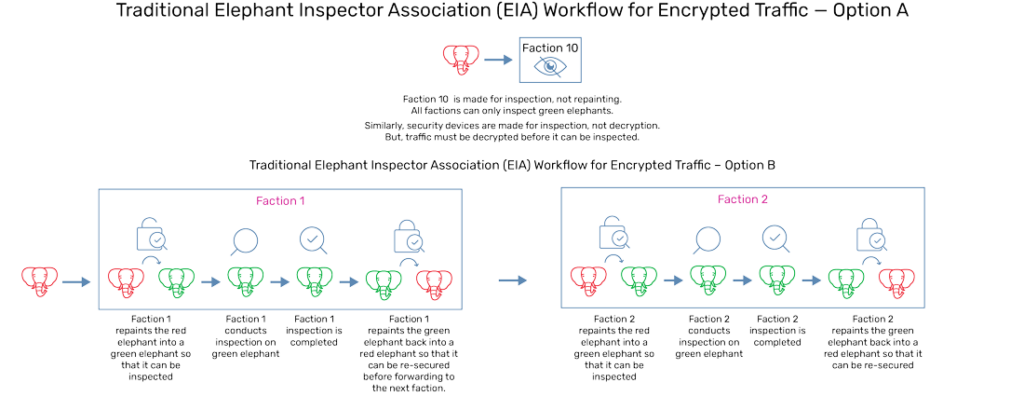
Fig 2: Traditional Elephant Inspector Association (EIA) Workflow for Encrypted Traffic – Options A vs. B
As you can see, the traditional method of inspection can be incredibly inefficient to undertake. To solve this, we add a new member to the team – faction 23 – which owns a secure zone. This is akin to the secure decrypt zone leveraged by Thunder SSLi – where all existing factions of the EIA can operate. The new workflow can be seen in figure 3.
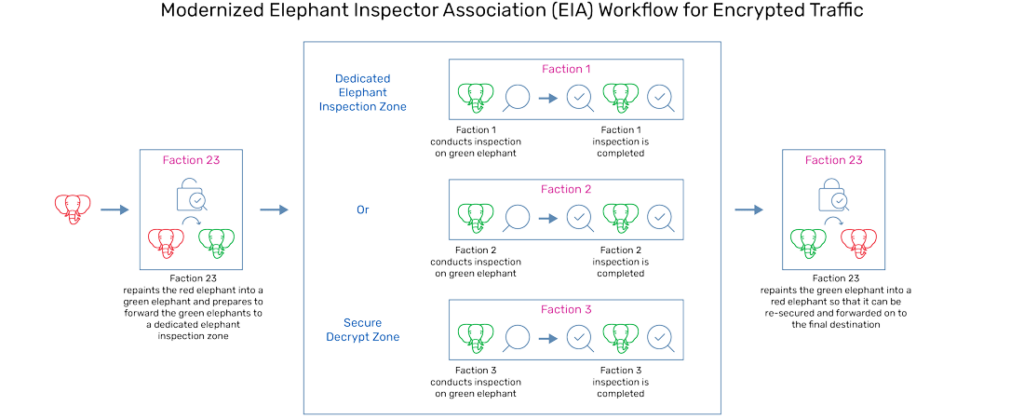
Fig 3: Modernized Elephant Inspector Association (EIA) Workflow for Encrypted Traffic
This method is much more efficient and secure because there is a secure zone, color transformation only occurs once, and the transformation capabilities are held within the hands of one entity instead of multiple. To tie this back to the decryption and encryption process, with Thunder SSLi, decryption and encryption only occur once, the secure decrypt zone ensures security, decryption keys aren’t handed out unnecessarily, and service-chaining allows for all existing security devices to perform their respective duties with scalability and efficiency.
For more detailed information about our expansive integration and comprehensive deployment capabilities, please engage with us. Download the Thunder SSLi datasheet, or take a listen to our on-demand webinars covering this subject.
A Real-world Application of the Thunder SSLi
Thunder SSLi and A10 Harmony® Controller, along with additional certificates and licenses, were leveraged to help with these pain points. Thunder SSLi provided a superior decryption performance across multiple protocols and ports while creating a secure decrypt zone that maximized the effectiveness of existing security devices. The AppCentric Templates simplified the deployment of Thunder SSLi. The integration of the URL classification and filtering service allowed for the creation of more granular access and control policies.
For example, on a webpage, all content was allowed, but the embedded YouTube video is blocked. Certain URLs can be crosschecked with a URL database to determine if the traffic is valid or not. In this case study, the additional integration of A10 Harmony Controller allowed for granular visibility and streamlined operations and management across a single pane of view.
The full-proxy-control nature of Thunder SSLi allows it to adapt to new unknown ciphers in the future. Additionally, it allows for control of bi-directional traffic. The deployment of Thunder SSLi, amongst other A10 products, proved to augment TLS decryption capabilities, enable flexible deployment options, and empower existing security devices to operate at maximum efficiency.
Thunder SSLi allows school to establish its Zero Trust security framework, with an overall lower TCO. Don’t overlook the importance of deploying a centralized and dedicated decryption solution. Satisfy this prerequisite and begin augmenting your enterprise security framework today!
Related Resources
- Traffic Inspection for Stronger Cyber Security (Report)
- Technology Company Gains Visibility into Encrypted Threats and Ensures Privacy and Security (Case Study)
- The Ultimate Guide to TLS/SSL Decryption (eBook)
- SSL Insight: Beyond Simple SSL/TLS Decryption (Video)
- Zero Trust is Incomplete Without TLS Decryption (White Paper)
- 5 Steps to Enhance Your Enterprise Security with High Performance SSL/TLS Decryption (eBook)