Why Roaming Still Matters in a 5G World

5G changes a lot, but not everything. While 5G security is a big step forward, vulnerabilities and risks still abound, especially when it comes to roaming. Why roaming? Because GPRS Tunneling Protocol (GTP), the legacy protocol that provides interconnect between multi-generational network interfaces, is inherently vulnerable. And as we’ll see later in this post, multi-generational networks (2G through 5G and beyond) will remain on the scene for quite some time, long into a 5G-exclusive or single-generation mobile technology universe ever comes about — if ever.
First, a bit about GTP
GPRS Tunneling Protocol (GTP) is a 2.5G technology that enables mobile users to roam seamlessly between networks of different generations. The protocol was developed alongside General Packet Radio Service (GPRS), the mobile data standard integrated into GSM that allows mobile networks to transmit IP-based communications to external networks.
As a 2.5G technology, GTP was not developed with 5G security in mind because, before the advent of smartphones, mobile networks had few, if any, 5G security issues. The proprietary technologies within what was then a largely closed industry made for mobile network infrastructures that were virtually “cyber attack free.” As the industry developed and IP-based technologies came to the fore, the need to secure GTP-enabled interconnections became critical, as evidenced by the increasing exploitation of GTP-exposed interfaces left vulnerable to cyber attacks. Mobile subscribers and operators alike are impacted, as cyber attackers tap into mobile communications to steal network information and subscriber IDs, which, in turn, can lead to service disruptions, customer churn, and fraud.
Roaming is on the rise
The elimination of international roaming charges and the skyrocketing number of applications, mobile subscribers who travel, and devices both smart and “stupid” (e.g., internet of things (IoT) and industrial internet of things (IIoT)) has led to exponential growth in roaming traffic — as much as 95 percent according to Telecoms.com. Billions of smartphones accessing mobile broadband and permanently roaming IoT devices with limited functionality and little or no security are driving mobile traffic data sky high. According to a recent Ericsson Mobility Report, such traffic, moving across almost 7 billion cellular devices connected worldwide today, is forecast to increase four-fold by 2025. And with next-generation infrastructure support for new device types and new use cases, the growth of international roaming traffic is expected to accelerate even more — Juniper Research predicts a 32-times increase by 2022.
As roaming increases so do the risks
As the volume of roaming traffic continues to grow, so do the risks. What’s at stake are new and emerging 5G mobile network revenue streams. To capitalize on the opportunities, mobile operators will need to solve 5G security challenges unique to 5G environments and today’s hyper-connected networks. In the 5G era, security will become an increasingly complex endeavor as the roaming ecosystem grows and becomes more diverse, opening up to a broader range of partners. With industry-specific Mobile Virtual Network Operators (MVNO) and IoT solution providers coming on board, mobile operators will find themselves confronting a security model built on aging protocols such as GTP rather than robust security. Cyber attack criminals are sure to see the potential of such a booming, yet vulnerable, target, and direct their hack and attack activities accordingly.
The persistence of multi-generational networks heightens the risks
Multi-generational mobile networks will exist long into the foreseeable future, which means that GTP will continue to be relevant in a 5G world. As with earlier generations, 5G introduces new standards. However, new standards do not replace the previous ones, but rather, they overlap. So as long as earlier generations remain operative, old protocols and their vulnerabilities will threaten networks, 5G or not. Mobile roaming has also changed radically over the course of the industry’s evolution. Today, more than 2,000 global partners participate in a web of interconnections supporting four generations of mobile technology through dozens of interfaces and protocols. As the industry moves to 5G, with significant overlap of 3G and 4G, new services and technologies will enlarge the attack surface.
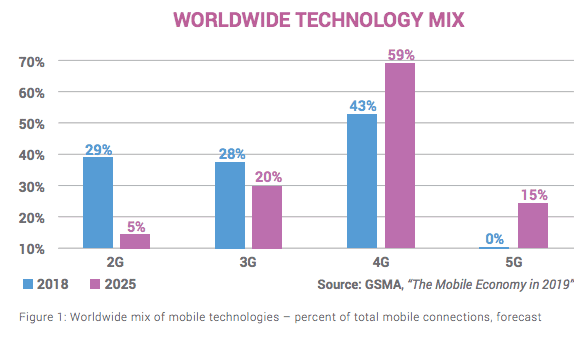
The GSMA estimates that only 15% of subscribers will be on 5G networks by 2025,
while 85% will continue to be served by 4G, 3G, and even 2G networks.
GTP-based attacks
GTP is a communications protocol, not a security standard. As such, it facilitates the flow of data within and between mobile networks, while leaving vulnerable network interfaces exposed to exploitation. GTP vulnerabilities make it easier for attackers to gain access to critical network and subscriber information, including key identifiers such as the Tunnel Endpoint ID (TEID) — a pathway into the network’s mobile core assigned by the GPRS Tunneling Protocol — GTP), the Temporary Mobile Subscriber Identity (TMSI), and the International Mobile Subscriber Identity (IMSI). That’s everything an attacker needs to impersonate a legitimate subscriber and breach a mobile network. Using such information, hackers can pilfer confidential data to commit fraud, overload networks, drop subscriber communications, and launch denial of service (DoS) attacks. Here’s how:
- Brute Force Attack (aka trial and error) – Using automated, brute-force tools, the attacker sends messages with arbitrary TEID values to the packet gateway until one proves successful. Then, again with brute force, the attacker captures the victim’s TMSI by passively scanning for it with the help of an eavesdropping device (e.g., an IMSI catcher — a rogue or fake base station). With the TEID and TMSI the attacker can send an identification request to the Mobile Management Entity, which will respond with the victim’s IMSI.
- IMSI Theft – Here, an attacker takes advantage of legacy 3GPP mobile standards that don’t require networks to authenticate devices and uses an IMSI catcher to steal the IMSI from an unsuspecting subscriber. The lack of authentication makes it relatively easy for an IMSI catcher impersonating a legitimate base station to capture the info needed to launch attacks.
Subscribers are often careless about protecting their smartphones and they expect to use their mobile devices and access all of their services on the road, especially now with recently enacted “Roam Like at Home” rules whereby people pay domestic prices for voice calls, SMS, and mobile Internet while travelling across the E.U. Plus, constantly roaming IoT devices are often unsecured. It all adds up to an environment that makes GTP-based attacks easier and more prevalent. For more information about the types of attacks enabled by GTP vulnerabilities, download the eBook: Smart Phones and Stupid Devices — Why Roaming Still Matters in a 5G World.
Industry beefs up 5G security — but is it enough?
5G architecture provides several important cyber security enhancements, including encryption, mutual authentication, integrity protection, privacy, and availability. Nevertheless, security will still be needed to protect against 2G, 3G, and 4G multi-generational threats during the transition to 5G. New 5G specifications cover security procedures performed within the 5G system, including the 5G core and the 5G New Radio.
Key 5G cyber security enhancements include a new Security Edge Protection Proxy that provides additional protection against known inter-exchange/roaming vulnerabilities. 5G also enables network operators to steer home customers to preferred visited partner networks to enhance the roaming experience and prevent fraud.
While 5G security is a big step forward, mobile networks will continue to be exposed to GTP threats. So mobile operators will need to deploy a GTP firewall to protect against attacks coming in from access networks, roaming partners, and IoT to support uninterrupted operations for their networks and subscribers.
Protecting 5G investments
With its high data rates and massive scale, 5G is raising the bar on the demands placed on operator networks. By enabling mobile broadband and ultra-reliable, low-latency communications, the technology will deliver the customer value needed to support long-term industry growth and profitability. However, massive 5G investments will remain at risk without the ability to protect customers, infrastructure, and mobile operators. Fortunately, most mobile operators are well aware of 5G security challenges and are taking a proactive approach to addressing them, as evidenced by a recent survey sponsored by A10 Networks.
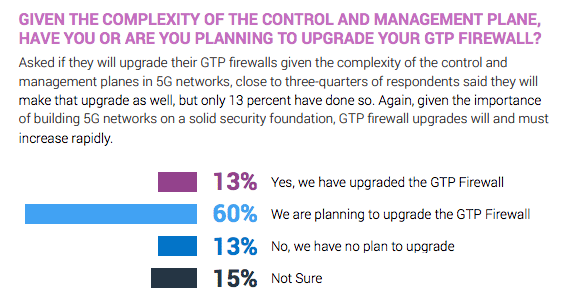
As they transition to 5G, 73% of mobile operators are planning to or have already upgraded their GTP firewall.
A10 Networks GTP Firewall
To fully capitalize on 5G opportunities, mobile operators need to ensure GTP security. A10 Networks GTP firewall protects the mobile core against GTP-based threats such as information leaks, malicious packet attacks, and DDoS attacks through GTP interfaces, providing the security and scalability needed to support uninterrupted operations. It leverages the latest standards and technologies to reduce vulnerability and prevent attacks, ensuring better mobile experiences for customers and a more profitable future for mobile operators.
Take a deeper dive
- Learn more about Mobile Roaming Security
- Download Smartphones and Stupid Devices — Why Roaming Still Matters in a 5G World