What is a Botnet (IoT Botnet)?
A botnet is a collection of internet-connected devices that have fallen under the control of cyber criminals to be used for their own malicious purposes. By using malware to infect a large number of vulnerable personal computers (PCs), servers, mobile devices, and internet of things (IoT) devices, “bot herders” can tap into vast amounts of aggregate computing power and functionality to launch an automated distributed denial of service attack (DDoS attack), perform data exfiltration, engage in engage in click fraud, and send spam emails, among other illicit schemes. In recent years, botnets have also played a growing role in cryptomining, as cyber criminals harness their resources for the massive processing power needed to coin cryptocurrency.
While botnets generally remain invisible to the users of infected devices, using only a fraction of the available resources, the impact of their activities can be devastating, as when a volumetric DDoS attack or protocol DDoS attack disrupts network services or knocks an entire network offline. Commonly offered for rent by cyber criminal organizations, botnets-for-hire have become a popular tool for hackers of all kinds, from disgruntled gamers seeking to undermine an opponent or disrupt a competition to university students hoping to delay an exam.
Building a Botnet
To create a botnet, a hacker uses malware such as Mirai to seek out devices with vulnerable endpoints. Any type of device will do—a smartphone or laptop, a smart home system, a network-attached storage device, a smart TV, anything that has an internet connection and weak security. As devices are recruited into this growing zombie army, they can be controlled by the bot herder using command and control (C&C) software over standards-based communication channels such as IRC and HTTP or peer-to-peer (P2P) connections. Once the botnet has reached critical mass, the bot herder can then operationalize its power to launch automated DDoS attacks, spam or click fraud campaigns, cryptomining operations, or data theft exploits.
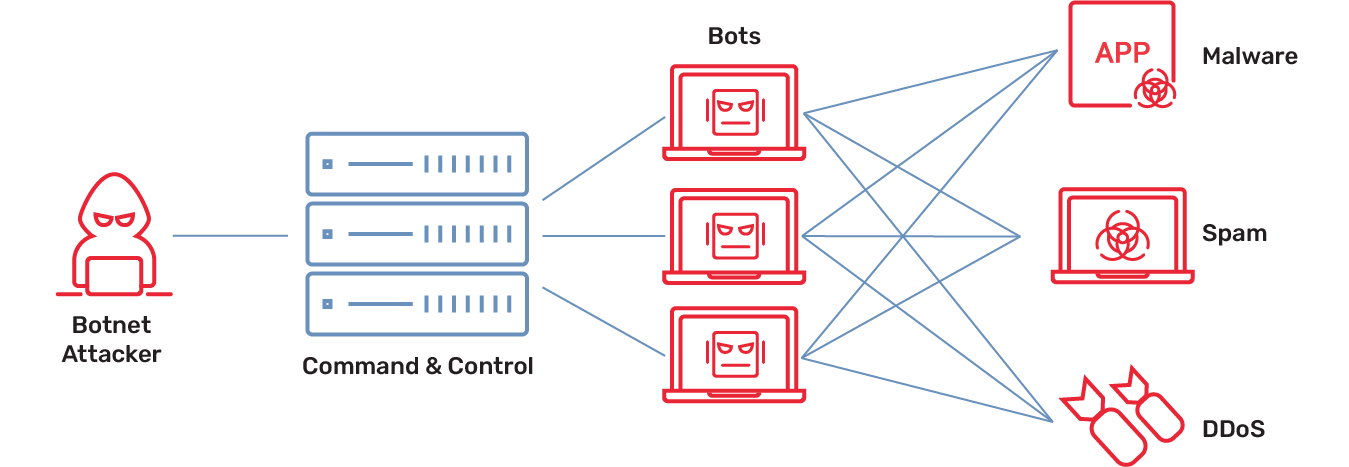
How a DDoS Botnet Works
Offering a massive, distributed base of internet-connected devices, a botnet is ideally suited for launching a distributed denial of service attack. In fact, DDoS attacks virtually always leverage a DDoS botnet. By sending a high volume of bogus traffic from each zombie device, the botnet can quickly overload the target network. As the web server struggles to handle the surge of requests, its processor cycles, network interfaces, and memory used for communications processing become exhausted, causing connections from normal traffic to be slowed down or even excluded.
In a volumetric DDoS attack, the DDoS botnet uses brute-force techniques to flood the target with data packets to consume bandwidth and resources. Increasingly, hackers seek to multiply the impact of a volumetric DDoS attack by leveraging the amplification factors of common protocols and services used across the internet. With this reflected amplification approach, the attacker sends multiple requests to these services spoofing the victim’s IP address, tricking servers into replying with large amplified responses. This tactic has resulted in record-breaking volumetric attacks, including a November 2021 DDoS attack on Microsoft that reached a throughput of 3.47 terabits per second. Volumetric DDoS attacks are often used as cover for other types of exploits, disabling the victim’s security infrastructure to make monitoring difficult or impossible.
A protocol DDoS attack relies on the weaknesses and complexity of internet communications protocols to compromise the target network. For example, Border Gateway Protocol (BGP) is used by network operators to announce to other networks how their address space in configured. By sending a fraudulent BGP update, a hacker can reroute network traffic to overwhelm and deplete targeted resources such as routers and firewalls. In 2018, hackers used BGP hijacking in conjunction with a DDoS botnet to redirect traffic intended for the MyEtherWallet, a service that managed Ethereum cryptocurrency accounts, to Russian servers to facilitate theft from cryptocurrency wallets.
The Rise of the IoT Botnet
The Internet of Things has been a boon for bot herders as a breeding ground for a denial of service attack. IoT devices are notorious for serious security issues, from weak or default passwords and lackluster security configurations, to open access to management systems and admin controls. Security patches are often neglected, especially in the case of consumer devices designed promising hands-free ownership. The networks through which they connect to the internet, such as home wifi systems, are typically unmonitored. These vulnerabilities make it all too easy for hackers to recruit these devices into an IoT botnet while remaining undetected for the long term.
Beginning in late 2016, a series of record-setting DDoS attacks were launched that researchers ultimately attributed to the Mirai IoT botnet. These included DDoS botnet attacks on the KrebsOnSecurity cybersecurity blog and Dyn DNS (Domain Name Service), and reached the then-unprecedented traffic level of one terabit per second. Designed to scan the internet for unsecured devices, Mirai would first attempt to log in using common default passwords before resorting to brute-force guessing. The subsequent public release of Mirai source code helped make the malware one of the most common mechanisms to recruit an IoT botnet. In the years since, Mirai variants have continue to proliferate, registering thousands of IoT botnet DDoS attacks against victims across professional, financial, and information services sectors.
Botnets and the Log4j Vulnerability
As one of the most prominent features of the cybersecurity landscape, it’s no surprise that botnets have played an important part in the Log4j vulnerability, the most serious security issue of recent years. Publicly disclosed in December 2021, the Log4j exploit is a flaw in the widely used Log4j open-source software package that can allow threat actors to mount remote code execution (RCE) attacks on the Apache Log4j Java logging library. Once the vulnerability was announced, hackers immediately put it to use. While some of these attacks were political in nature, Log4j also proved highly popular as a mechanism to perform large-scale scanning for vulnerable sites to create crypto mining and DDoS platforms.
Within weeks, Mirai IoT botnets were using the Log4j vulnerability to recruit devices including IP cameras, smart TVs, network switches, and routers. Since then, two additional botnets, Elknot (also known as the BillGates trojan) and the Gafgyt (BASHLITE), have also been detected using the Log4j exploit as a denial of service attack platform. While updated versions of Log4j have been available to close the Log4j vulnerability since shortly after its disclosure, the implementation of these patches across the industry remains an all-too-slow work in progress.
Leveraging Zero Trust and Threat Intelligence for DDoS Protection
As proliferating botnets—especially IoT botnets—intensify the denial of service threat, organizations are redoubling their focus on DDoS protection. The Zero Trust framework is an important element of this effort, helping to ensure that networks are not being weaponized through a “never trust, always verify” philosophy.
Continuous checks throughout the network help ensure that resources are accessed only by authenticated and authorized users and accounts, complemented by micro-segmentation, micro-perimeters, comprehensive visibility, analytics and automation, and a well-integrated security stack.
Beyond Zero Trust, threat intelligence is crucial to prevent a denial of service attack. Timely data about current DDoS activity, such as the IP addresses of DDoS botnets and available vulnerable servers commonly used for DDoS attacks, leveraged in conjunction with real-time threat detection, artificial intelligence (AI)/machine learning (ML) capabilities, and automated signature extraction, can enable organizations to take a protective approach to DDoS attack mitigation.
How A10 Networks Mitigates DDoS Attacks Caused by Botnets
A10 Defend provides a holistic DDoS protection solution that is scalable, economical, precise, and intelligent to help customers ensure optimal user and subscriber experiences. With the IoT-based DDoS attacks growing, our DDoS protection solution ensures continued availability of services in demanding times.
A10 Networks’ security researchers are at the forefront of DDoS weapons intelligence, including the definitive annual DDoS Threat Report. A10 delivers a comprehensive and converged system to enable organizations to achieve full-spectrum DDoS protection.
Botnet/IoT Botnet Articles of Interest
- When the Internet of Things (IoT) is Armed as an IoT Botnet
- Should You Fear the Reaper Botnet?
- Protecting Against WireX Botnet DDoS Attacks
- Inside the Mirai Malware That Powers IoT Botnets
- Secure your Online Sales from Cybersecurity Threats during the Holiday Season
- Load Balancing Goes to School to Learn Application Availability
- How to Defeat Emotet Malware with SSL Interception