How to Defend Against Amplified Reflection DDoS Attacks

What are Amplified Reflection DDoS Attacks?
Amplified reflection attacks are a type of DDoS attack that exploits the connectionless nature of UDPs with spoofed requests to misconfigured open servers on the internet. Amplified reflection attacks take the prize when it comes to the size of the attack.
The attack sends a volume of small requests with the spoofed victim’s IP address to accessible servers. The servers reply with large amplified responses to the unwitting victim. The servers can do this because they are configured with services that the attackers sought out for their ability to aid in this attack.
This video below from nat0 provides a short introduction to this type of DDoS attack. This article provides a more detailed explanation of amplified reflective UDP-based attacks.
The most common types of these attacks can use millions of exposed DNS, NTP, SSDP, SNMP and other UDP-based services. These attacks have resulted in record-breaking colossal volumetric attacks, such as the 1.3Tbps Memcached-based Github attack, and account for the majority of DDoS attacks. The chart in Figure 1 below shows how nearly 73% of the DDoS attacks during a week in July 2018 have been amp_flood. Here you will find the current attack protocol frequency chart.
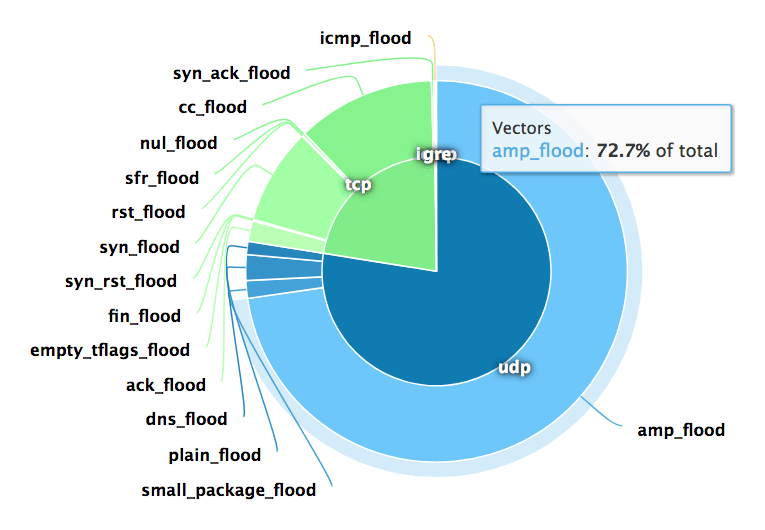
Figure 1: Attack Protocol Frequency
Attackers love this strategy because the weapons are persistently available, difficult to attribute to the orchestrator, and require little effort to create huge volumetric attacks using a small pool of bots or a single powerful server.
Weapons Used in Amplified Reflection DDoS Attacks
Earlier, the tools being exploited were referred to as “misconfigured open servers.” A better description is “poor management hygiene.” Servers may fulfill a specific purpose for the owner who deployed them but have no access controls in place, or may have been forgotten and left unmanaged, or may have been unintentionally exposed to the internet for no apparent reason.
For example, there are about 3 million SSDP servers repeatedly used for DDoS attacks that have amplification factor greater than 30x. What the heck were the owners thinking when they exposed UPnP functionality to the internet? But that is the dirty cyberworld we live in.
Memcached servers are especially notable on this list of UDP amplifiers due to its huge amplification factor-a possible 51,000x of the spoofed request. At the time of the Github attack, there were approximately 300K exposed Memcached servers.
The table below provides an exploitable UDP service and its amplification factor. Most of the the data in this table can be found in the National Cybersecurity and Communications Integration Center’s Alert (TA14-017A): UDP-Based Amplification Attacks.
Table 1: Exploitable UDP Service and Amplification Factor
| Type | Amplification Factor |
|---|---|
| Memcached | 10,000 to 51,000 |
| NTP | 556.9 |
| CharGEN | 358.8 |
| QOTD | 140.3 |
| RIPv1 | 131.24 |
| CLDAP | 56 to 70 |
| LDAP | 46 to 70 |
| DNS | 28 to 54 |
| Quake Network Protocol | 63.9 |
| TFTP | 60 |
| SSDP | 30.8 |
| MSSQL | 25 |
| Kad (P2P) | 16.3 |
| Portmap (RPCbind) | 7 to 28 |
| SNMP | 6.3 |
| Steam Protocol | 5.5 |
| NetBIOS | 3.8 |
| BitTorrent | 3.8 |
| Multicast DNS (mDNS) | 2 to 10 |
Memcached Servers Continue to be Exploited
The internet has improved since the early days. Owners are reducing the number of servers down to about 40 thousand. However, those Memcached servers continue to be exploited. Figure 2 below from the Network Security Research Lab at Qihoo 360 provides valuable insights into the Global DDoS Threat Landscape. During the period from May through July 2018, memcache has shown it continues to be a significant portion of DDoS attacks.
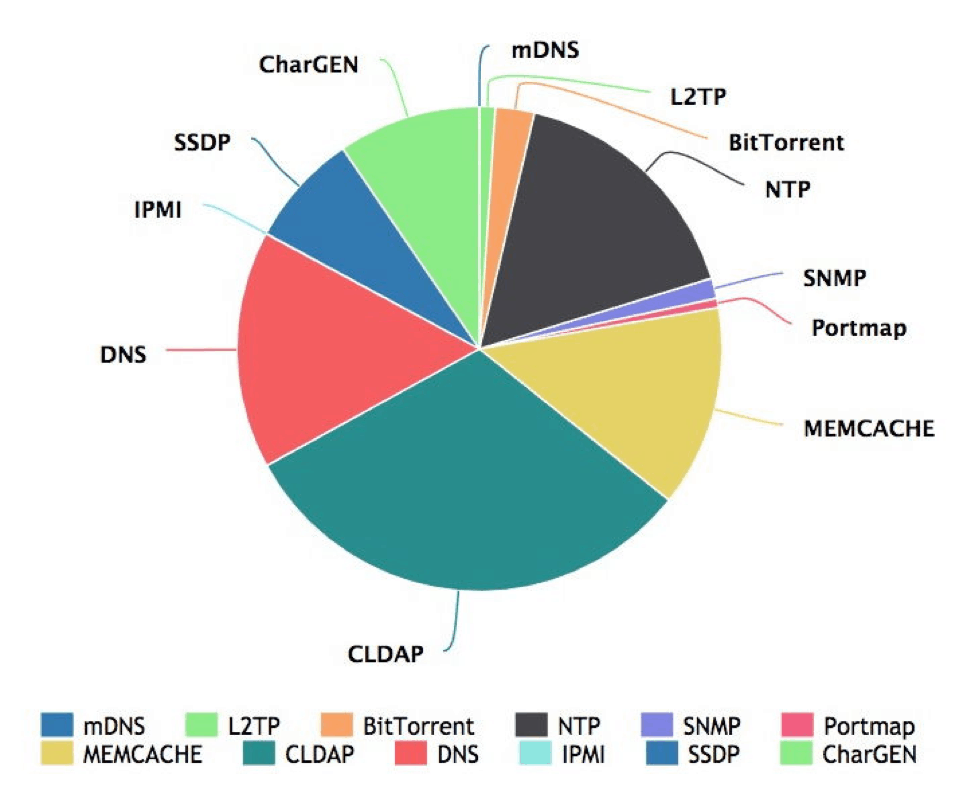
Figure 2: Frequency of Protocols Used for Reflection
Defenses for Amplified Reflection DDoS Attacks
Detecting a reflected amplification attack is easy, given the boisterous nature of volumetric attacks. However, mitigating an attack is not as easy, because the responses come from legitimate sources that follow RFC structure and use some of the services that provide functions users depend on, like DNS and NTP.
The challenge is to surgically distinguish legitimate user workloads from reflected traffic. In many cases, a service under attack will see additional legitimate user traffic due to repeated retries in response to the sluggish response of that service. These retries can be mistakenly seen as DoS behavior.
Four Strategies for Mitigating Amplified Reflection DDoS Attacks
1. Rate limiting
Rate limiting is a general category of DDoS mitigation strategies. The limits can be applied to destinations or to sources. Destination rate limiting is fraught with collateral damage due to its indiscriminating nature and should only be applied as a last course of action to prevent the system from falling over. Rate limiting the source is more effective, as it is done based on a deviation from a set access policy. Restricting these noisy sources or even dropping the UDP fragmented packets from these sources will greatly reduce the impact.
2. Regular Expression (Regex) filter
Applying traffic signature filters can be an effective defense against reflected amplification attacks. These attacks have identifiable repetitive structures from which a regular expression can be derived.
One drawback of Regex filtering may be performance. DDoS defenses sit at the edge of the networks and must absorb the full volume of a business’s internet capacity. Regardless of whether the inspection is done in software or hardware, inspecting every packet may overwhelm the defenses.
3. Port Blocking
Blocking unneeded ports is always good security practice. The challenge is defending ports that are shared by both legitimate and attacker traffic. DNS’s TCP or UDP port 53 are good examples of required ports that are commonly attacked. Blocking port 53 would have the same effect as a DoS attack on everyone in the environment. On the other hand, blocking port 1900 traffic sourced from the internet makes a lot of sense, since SSDP is an unlikely legitimate use case across the internet.
4. Threat intelligence
Attackers continuously scan the internet looking for servers to employ in their DDoS campaigns. The identity of these vulnerable servers are available to as real-time feeds from threat intelligence companies.
Knowing and then blocking the IP address of vulnerable servers is an effective, proactive way to mitigate attacks. This strategy uses reputation as a determining factor for blocking traffic, enabling more precise mitigation. The challenge is taking voluminous feeds of tens of millions of entries and making them actionable.
For example, after the Spamhaus DNS amplification attack in 2013, at the time a record-breaking 300Gbps, the Open DNS Resolver Project was started to instill good internet hygiene and wipe out the approximately 28 million exposed DNS servers that responded to unauthenticated DNS queries with type “ANY”. The IP addresses of those servers were knowable then and continue to available today.
In fact, A10’s DDoS threat intelligence map identifies about 4 million servers that are still vulnerable and being used in DNS reflected amplification attacks today.
Methods for Blocking Each Type of Amplified Reflection Attack
Choosing an effective defense strategy requires finding the right balance between effectiveness, cost to implement, and avoiding collateral damage to legitimate users.
Table 2: Port Blocking and Threat Intelligence Use Cases
| Reflected Amplified Attack Type | Attack Source Port | Recommended Mitigation Strategy |
|---|---|---|
| BitTorrent | UDP 6881 | Block source port |
| CharGEN | UDP 19 | Block source port |
| CLDAP | UDP 389 | Block source port |
| DNS | UDP 53 | Threat Intel |
| Kad (P2P) | UDP 751 | Block source port |
| Memcached | UDP 11211 | Block source port or Threat Intelligence |
| MSSQL | UDP 1434 | Block source port |
| Multicast DNS | UDP 5353 | Block source port |
| NetBIOS | UDP 137 | Block source port |
| NTP | UDP 123 | Block MONLIST responses or Threat Intelligence |
| Portmap (RPCbind) | UDP 111 | Block source port |
| QOTD | UDP 17 | Block source port |
| Quake Network Protocol | UDP 27960 | Block source port |
| RIPv1 | UDP 520 | Block source port |
| SNMP | UDP 161 | Block source port or Threat Intelligence |
| SSDP | UDP 1900 | Block source port |
| Steam Protocol | UDP 27015 | Block source port |
| TFTP | Ephemeral | Threat Intelligence |
How A10 Can Help
Reflected amplification attacks are a menace that continues to grow. As the industry innovates with new applications and services, attackers find new tools to exploit. As defenders, understanding attack strategies and knowing where an attack will come from can give us the upper hand to achieve DDoS resilience.
Applying aggressive port blocking and blacklisting IPs based on reputation carries a certain level of risk. Legitimate users can become collateral damage. For example, an IPv4 address could be shared by a vulnerable server and potential legitimate user via NAT services. However, during a DDoS attack, suspected traffic must be removed to prevent the targeted system from falling over.
To minimize collateral damage against legitimate users, A10’s Thunder TPS DDoS mitigation product has an innovative five-level automatic mitigation escalation strategy. This strategy lets DDoS defense operators apply predefined mitigation strategy at appropriate levels. For example, at peacetime, or what we call Level 0, no mitigation is enforced. When an attack is detected, our system automatically escalates to Level 1 though Level 4. Port blocking or threat intelligence can be assigned to any of the levels as an automated dynamic policy after other less invasive techniques have been exhausted.
Our actionable DDoS Threat Intelligence provides you large numbers of IPs that map the huge numbers of weapons available to attackers. Many of the vulnerable services have millions of individual IPs, as you can see in our A10’s DDoS Threat Intelligence Map. This DDoS Threat Intelligence is included with our Thunder TPS product, supporting the largest available class-lists of up to 96 million entries.
Learn more information about A10’s DDoS protection solutions.