What is a Web Application Firewall (WAF)?
Enabling Secure Application Delivery for Web Applications
A web application firewall (WAF) is a specialized form of application firewall designed to enable secure application delivery for HTTP-based applications. As these applications become more prevalent, organizations have deployed WAF functionality to inspect network traffic at the application layer, a more granular level than traditional network firewalls. Deployed as a standalone hardware or software device, or through an application delivery controller (ADC) or server load balancing (SLB) solution, a WAF helps prevent attacks exploiting vulnerabilities such as SQL injection, cross-site scripting (XSS), cross-site request forgery, and improper system configuration.
The Development of the Web Application Firewall
Firewalls have been a foundational element of network security since the early days of widespread internet connectivity. By monitoring incoming and outgoing traffic between systems or networks based on a set of rules, a firewall enables an organization to reduce the risk of attacks or breaches.
As web applications became more common in the late 1990s, and web server attacks increased accordingly, security vendors introduced dedicated WAF devices to reduce the risk associated with these more publicly exposed applications. In addition to commercial solutions, the open source project ModSecurity was formed in 2002 by Trustwave’s SpiderLabs to expand access to both WAF technology and a standard set of rules to protect against the Open Web Application Security Project’s (OWASP) annual web application vulnerability Top-10 List. With the cyberthreat landscape continuing to intensify, and regulations such as the Payment Card Industry Data Security Standard (PCI DSS) and the EU General Data Protection Regulation raising the cybersecurity standards requirements for compliance, the WAF market has been projected to reach $13.8 billion by 2027.
How the WAF Fits into Application Delivery
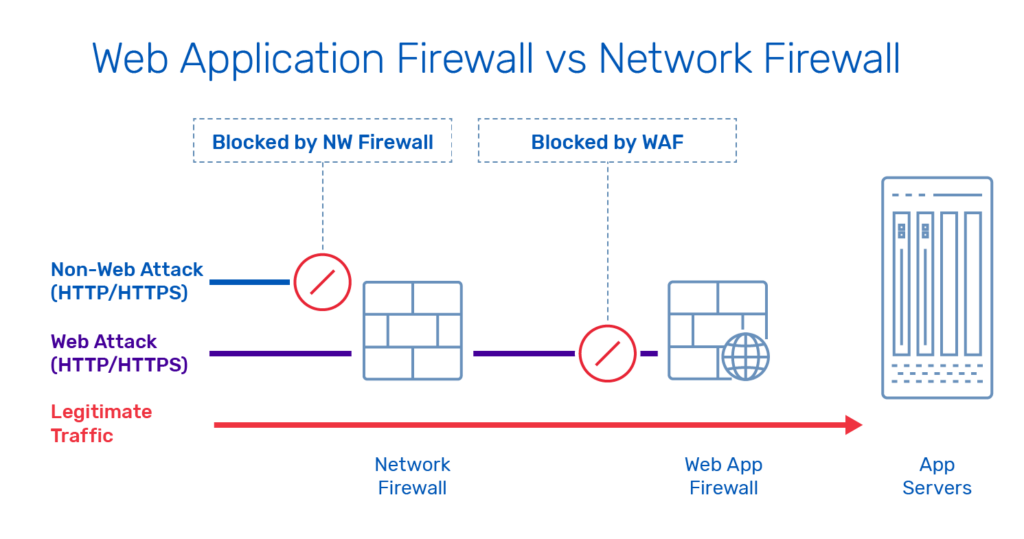
As its name suggests, a web application firewall monitors, filters, and blocks data packets as they travel to and from web applications. The WAF can be deployed in the network, on the host, or in the cloud, in front of one or more web applications or websites. While it can theoretically be deployed anywhere in the data path, it should optimally be positioned behind the server load balancing (SLB) tier and close to the application server it is protecting.
Unlike proxies, which protect clients, WAFs protect the server itself, typically functioning as a reverse proxy. Working at Layer 7 of the OSI model, the application layer, the WAF inspects and analyzes data packet elements such as the user-agent, headers, referrer, redirects, and HTML body according to defined rules, and filters out potentially harmful traffic before it reaches the server.
Combining WAF with Server Load Balancing in an Application Delivery Controller
While web application firewall solutions were once typically standalone point products, they are increasingly integrated into other elements of the application delivery infrastructure. The integration of a WAF into an application delivery controller has proven especially popular and effective. Typically situated at the border between the data center and the internet, the application delivery controller is well positioned to host functionality to screen network traffic for threats to web applications alongside other functions such as DDoS protection, SSL offload, content caching, and server load balancing.
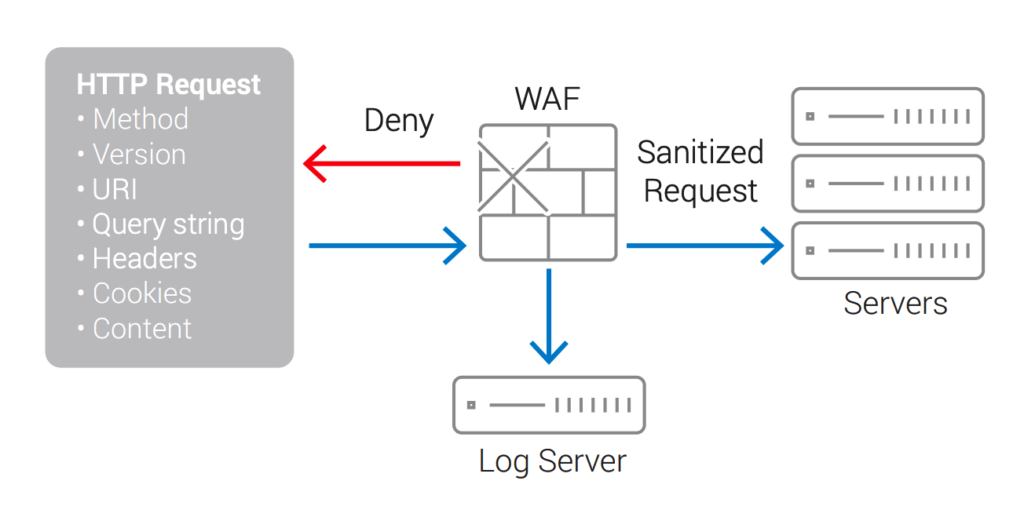
Thunder ADC and CFW, with their integrated WAF, can block attacks, sanitize requests of malicious content and log activity.
The benefits of combining WAF and ADC functionality can be considerable. Occupying a privileged position of trust and oversight in the network topology, an application delivery controller gets a complete view of the whole OSI model from Layer 2 – Layer 7 and can add value by performing the role of a WAF as well. In some cases, organizations choose to use a load balancer to implement WAF functions; conversely, a web application firewall can also assist with server load balancing by examining HTTP traffic before it reaches the application server. In fact, the most complete next-generation web application firewall solutions can incorporate advanced security features such as intrusion prevention and threat intelligence in addition to server load balancing.
Using a WAF for Cyber Attack Mitigation
As zero-day exploits, malware infections, impersonation, and other known and unknown threats and vulnerabilities attack web applications, organizations rely on the WAF for secure application delivery to an increasingly distributed workforce. This also affects customers using public-facing web applications such as e-commerce, online banking, telehealth, and streaming media.
Key threats defended by a WAF can include:
- SQL injection attacks using a web form to send SQL commands, or commands containing SQL special characters, that trigger the backend SQL database to allow unauthorized users access sensitive company data, modify database data, and execute administration operations on the database
- Cross-site scripting (XSS) in which a web server fails to validate data coming from another site, enabling the attacker to obtain sensitive information or otherwise compromise the server
- Sensitive data exposure where inadequately secured web applications permit attackers to exfiltrate personally identifiable information (PII), protected health information (PHI), and other sensitive or regulated data
- Cross-site request forgery attacks in which a fraudulent user HTTP request, including the victim’s session cookie, is sent to a vulnerable web application to steal the victim’s data, hijack their account, or perform other illicit functions
- Buffer overflow attacks where a hacker manipulates a coding error to overwrite an application’s process memory fragments and cause exceptions and other errors to undermine the application’s security
A WAF can provide cyber-attack mitigation for a web application vulnerability in several ways. HTTP content can be filtered through whitelisting, blacklisting, or a combination of the two, using information about known malicious or known safe IP addresses to determine which packets should be passed to the web application server. To prevent buffer overflow attacks, a WAF can set accepted maximum thresholds for aspects of HTTP requests and block requests that exceed these limits. To deter other types of threats, the WAF can strip HTTP response headers to hide the web server information needed to target an attack effectively.
Web application firewalls played an important role in mitigating the Log4j vulnerability. Soon after disclosure of the Log4J vulnerability on December 10, 2021, network security vendors published prevention signatures for WAFs to use to screen for and block Log4j exploits. In many cases, WAF rules were updated automatically by the vendor, helping to reduce risk in the face of a truly historic cybersecurity crisis.
While the web application firewall plays an important role in cybersecurity, it’s important to note that a WAF is not intended or designed to be a complete security solution. Instead, it works in conjunction with other elements of the perimeter security stack as part of a multilayered strategy to detect, prevent, and mitigate cyberthreats.
How A10 Networks Delivers Web Application Firewall (WAF) Functionality
A10 Thunder® Application Delivery Controllers (ADCs) include a full-featured WAF that blocks web attacks before they can reach vulnerable applications. Deployed as a proxy in front of web servers, Thunder ADC inspects web requests and responses and can block, sanitize, or log malicious activity. Designed to recognize many of today’s threats, Thunder ADC also offers flexibility to customize checks for emerging threats. By delivering integrated WAF, application delivery controller (ADC), and server load balancing (SLB) functionality, Thunder ADC provides a highly scalable security solution with high performance, simple configuration and administration, and low total cost of ownership.
Related Resources
- Thunder Web Application Firewall (Solution Brief)
- Driving Digital Transformation with Effective Application Delivery and Security (Blog Post)
