Three Keys to DDoS Protection: Monitor, Protect, Communicate

In late 2016, the DDoS landscape changed. The Mirai botnet was responsible for the first DDoS attack on record to exceed 1 Tbps. Before that, the largest was around 600 Gbps.
In the video below, A10 Networks Director of Product Marketing Paul Nicholson discusses DDoS trends and offers DDoS protection tips:
At the same time, the overall size and frequency of DDoS attacks continued to climb. A recent IDG Connect report commissioned by A10 found attacks of greater than 50 Gbps have more than quadrupled and companies experiencing between six and 25 attacks per year has ballooned by more than four times since 2015.
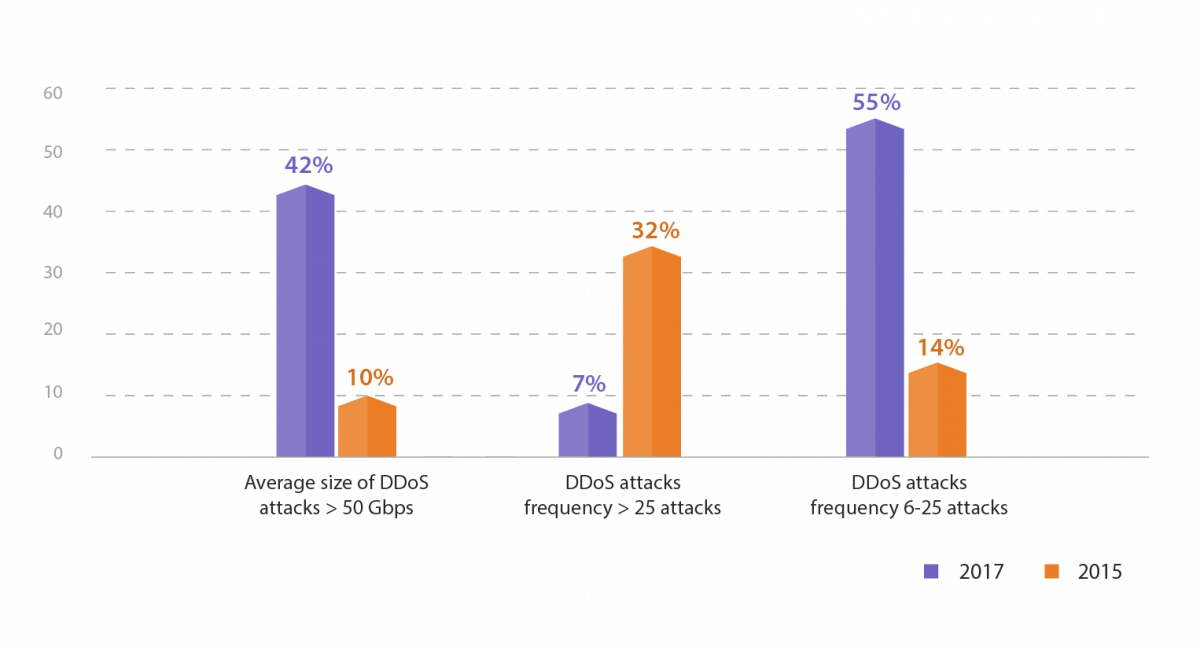
This growth has sparked a renewed sense of urgency. It’s altered the economics of DDoS protection, as most legacy DDoS defense solutions can’t scale to mitigate large and frequent attacks.
And it’s prompted security pros to reevaluate their DDoS protection and seek solutions that not only scale, but that can also help alleviate the stress of being in the attack crosshairs.
Here are three keys to DDoS defense that will help security pros sleep better at night, and ensure your networks and applications are protected against modern DDoS attacks:
Monitor and Detect DDoS Threats
You can’t fight what you don’t know is there. Monitoring your network traffic and flow data with DDoS detection alerts security pros to anomalies before they become full-blown catastrophes.
One way to get a better understanding of what’s happening on your network is baselining to know what your traffic looks like during peacetime, so when an attack happens you can take the appropriate wartime countermeasures.
A10 Thunder TPS Detector can monitor 500,000 flows per second – that’s double the flows of our competitors. And it can detect attacks within 3 seconds and automate DDoS protection procedures to put mitigation in place. But it’s not just about processing the data, it’s about the ability to quickly make intelligent decisions with that data.
DDoS Mitigation and Protection
DDoS protection requires having the right mitigation in place. Modern DDoS solutions empower you to automate defenses. You can automate anything from reports to packet captures to mitigation. This can help security pros reduce stress and thwart attacks quickly.
A10 is known for our high levels of mitigation. Many of the largest, most important networks in the world – cloud providers, service providers, gaming providers, mobile carriers and enterprises – trust A10 to protect their networks. With 300 Gbps in a single three rack-unit box, and 440 MPPS, along with the ability to scale above 2 Tbps in a cluster, you get the most bang for your buck with A10’s Thunder TPS DDoS detection and mitigation product.
And aGalaxy management for Thunder TPS ensures you have the right policies in place to automate and manage attack responses to minimize their impact and cast them out quickly.
DDoS Attack Communicate Plan
As with all security procedures, effective DDoS defense involves a human element, as well. Having a communication plan in place in the event of an attack is imperative.
Who you notify during and after an attack is critical. For example, who do you notify if the site goes down due to a DDoS attack? Is that the same person you’d notify if a DDoS attack takes out a gaming service? Who else is notified if an attack happens? Having communications ironed out ahead of time can reduce time to remediation and lower stress levels.
Overall, these three keys are about detecting, mitigating and communicating attacks with speed and stopping them before they wreak havoc.
For more information on A10 Thunder TPS, see our data sheet.
Seeing is believing.
Schedule a live demo today.