What Service Providers (and Enterprises) Need to Know About DDoS Scrubbing Services

There are a number of considerations that service providers must make when implementing DDoS scrubbing services for their subscribers. In general, those considerations fall into three categories: business, technical and economic.
In this article, we’ll cover all three of those categories. You’ll learn about:
- Business Considerations – DDoS Trends
- Technical Considerations – DDoS Defense Deployment Options
- Economic Considerations – Deploying Profitable DDoS Scrubbing Solutions
Then, we’ll look at a couple of case studies that show how these considerations have helped service providers improve their services, increase adoption and improve subscriber stickiness.
Keep reading to discover what service providers should be thinking about before deploying a DDoS scrubbing service, as well as the considerations that enterprises should make while picking a communication service provider (CSP) as their DDoS protection provider.
Business Considerations – DDoS Trends
As DDoS attacks have evolved, they’ve become a triple threat in terms of length, strength and sophistication.
- Length: While the relative year-over-year frequency of DDoS attacks has stabilized, DDoS attack duration continues to increase with each passing year.
- Strength: Unfortunately for their targets, DDoS attacks are growing in strength, as well as duration. A report from A10 Networks and IDG revealed that the frequency of attacks greater than 50 Gbps quadrupled.
- Sophistication: DDoS attacks are only becoming more sophisticated with time, and it’s no longer uncommon for attackers to use DDoS attacks as a smokescreen for a multi-vector attack strategy. What’s more, large companies are no longer the only ones being affected by devastating attacks. One study conducted by the Ponemon Institute and sponsored by Keeper Security found that 26 percent of small- and medium-sized businesses experienced a denial-of-service attack in 2018, up from 21 percent in 2016.
Ironically, one reason organizations become unsuspecting victims of DDoS attacks lies in their efforts to embrace ever-evolving networking trends and transformations without making the necessary accommodations in their security posture.
Here are a few examples of such transformations that, if not properly implemented, can accidentally leave organizations, especially enterprises, more vulnerable:
- A widespread shift to cloud-based services
- A greater focus on white box (non-brand name) hardware
- Increased integration of open source software
Keeping in pace with these trends, DDoS service capabilities and implementation strategies need to be updated, as well. If they aren’t, the results could be devastating for service providers and enterprises alike.
Technical Considerations – DDoS Defense Deployment Options
Enterprises typically have four major options for DDoS defense:
- Firewalls (FWs), intrusion detection systems (IDS) and intrusion prevention systems (IPS)
- Cloud scrubbing
- Communication service provider (CSP) scrubbing
- Hybrid DDoS protection
While one cannot discount the importance of using FWs, IPS and IDS in a network, their use as dedicated DDoS mitigation solutions should be highly discouraged.
When CPSs provide DDoS scrubbing services to enterprises to remove malicious traffic, both CSPs and their subscribers can benefit.
First, CSP scrubbing is a less expensive option for the enterprise. Moreover, it doesn’t involve redirecting traffic through several extra hops like one would in the case of cloud scrubbing solutions. Thus, from a network latency perspective, one avoids incurring the extra expense by executing DDoS scrubbing natively within the CSP network.
On top of that, as we’ll see in the case studies presented later, CSPs that offer scrubbing services stand to gain additional profits, improve subscriber stickiness and increase customer/subscriber satisfaction.
So, why don’t all CSPs offer scrubbing services? It all comes down to common practical limitations:
- Lack of trained staff required to manage a security operations center (SOC)
- Expenses required to scale a DDoS defense platform
- Limited budgets of CSPs’ subscribers
However, a modern approach to DDoS defense can help CSPs overcome those challenges.
Economic Considerations – Deploying Profitable DDoS Scrubbing Solutions
In order to offset the challenges associated with providing DDoS scrubbing services, CSPs should prioritize two strategies:
- Implementing effective, automated DDoS mitigation solutions
- Scaling of profits and differentiated services
Together, these strategies will make it possible to build scrubbing services that are both profitable and scalable.
Effective, Automated DDoS Mitigation Solutions
When building a DDoS scrubbing service, it’s essential to eliminate manual intervention whenever possible. Attackers are taking advantage of the benefits of automation, so it only makes sense for defenders to follow suit.
A scaled-up task force is not an effective economic solution to address the rise in DDoS attacks. Instead, DDoS mitigation solutions should be able to automatically detect, mitigate and report DDoS attacks. As simple as this choice sounds, one should note that not all DDoS mitigation solutions are built alike.
Remember, the main objectives of DDoS defenses are to ensure:
- Continuous availability of service for valid users
- Continuous availability of services and infrastructure
While these two objectives may sound one and the same, there’s a subtle difference here that is important to appreciate.
DDoS mitigation solutions that indiscriminately restrict both legitimate and illegitimate traffic may be able to ensure continuous availability of services and infrastructure, but they don’t always ensure access for valid users.
For that reason, it’s crucial that CSPs looking to implement a DDoS mitigation solution seek out a solution that can distinguish between users that are valid and those that aren’t.
Such an automated solution will have to use multi-modal detection and mitigation strategies, including:
- Automatically applying countermeasures that adapt to today’s ever-morphing DDoS attacks
- Recognizing and mitigating zero-day attack patterns
- Leveraging DDoS weapons intelligence and taking action on known bad actors

With all three of those capabilities in place, a fully automated defense system will be able to drop illegitimate traffic and serve legitimate users, while protecting services from DDoS attacks. Across the entire protection cycle, intelligent automation will look something like this:
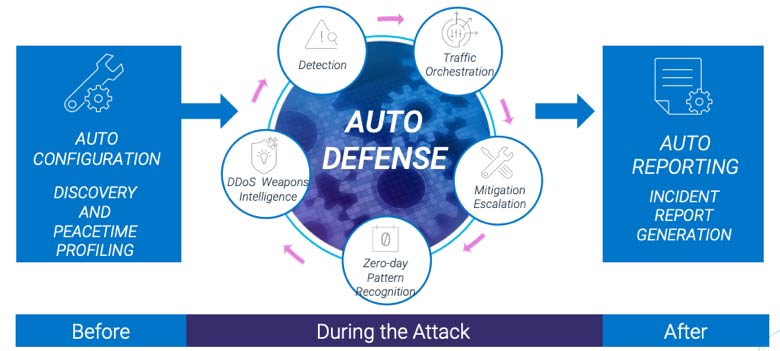
Automated DDoS defenses can also significantly cut down on response times. The speed at which such a system can respond to threats far exceeds that of a manual system, a study from NimbusDDoS discovered:
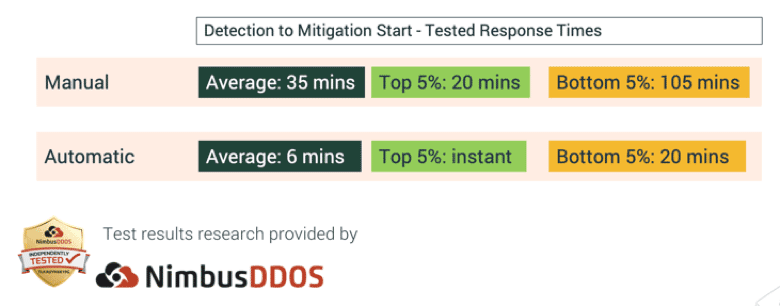
Given that 37 percent of organizations are looking for a DDoS defense system with speedy response times, CSPs have a much higher chance of increasing their subscriber/tenant base when offering automated DDoS mitigation solutions on their network.
Scaling of Profits and Differentiated Services
In order to build profitable scrubbing services, service providers must also ensure that their DDoS mitigation solution provides:
- A high number of detection policies
- A high number of simultaneous mitigations
- Differentiated services
The ability to support more detection policies and simultaneous mitigations on a single platform means that one is able to onboard that many more tenants on a single platform. This means higher profit margins for service providers.
However, being able to onboard multiple tenants is only possible if every subscriber feels that the CSP is providing a differentiated DDoS mitigation service that is geared towards their needs.
In terms of differentiated services specifically, it’s important to remember that all of the tenants in a service provider’s environment are running different businesses. None of them have the exact same level of risk tolerance, available budget or business model.
That’s why the most successful DDoS scrubbing services will be differentiated into multiple tiers, from budget to premium:
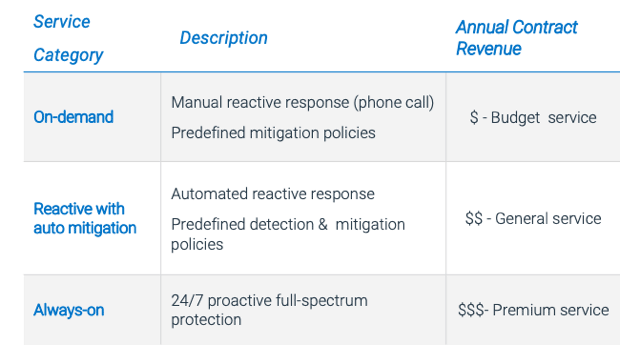
In this way, a CSP’s tenants will get more flexibility and the CSP will be able to sell DDoS mitigation services to a wider subscriber base.
As an example, let’s take a look at the deployment diagram of DDoS scrubbing services:
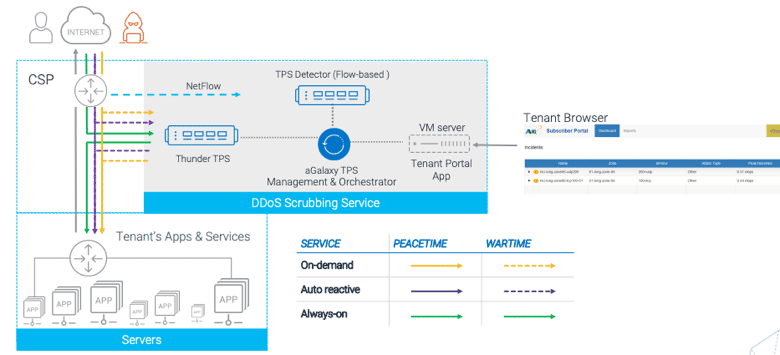
Notice these key elements:
- A centralized scrubbing service inside of the CSP’s environment
- A portal for tenants where each tenant can see what’s going on in their own network
- During peacetime, traffic flows from the internet through the router over to the tenant’s services. In the case of always-on traffic, traffic is always redirected through the DDoS scrubbing service before reaching the servers.
- During wartime, all traffic is redirected through the scrubbing service before reaching the tenant’s servers.
Case Studies: How Two CSPs Saw Major Results from Implementing DDoS Scrubbing Services
Finally, let’s examine how CSPs can benefit from providing DDoS scrubbing services by reviewing a couple case studies.
Leaseweb
Leaseweb is a web hosting company with a strong global presence. The company aimed to set up a DDoS scrubbing service and IP protection system in order to thwart attacks and better retain subscribers.
The company successfully built a DDoS defense system for their own infrastructure, as well as offering DDoS scrubbing services to their business tenants.
When selecting their DDoS IP protection system, Leaseweb had to meet a list of criteria:
- Global availability
- Protection of individual IP addresses
- Integration into and automation with Leaseweb systems
- Highest reliability with the lowest impact on performance
- 24×7 support and a security operations center
After running their system with A10 Networks’ Thunder® TPS DDoS mitigation solution for 90 days, during which time it scrubbed more than 25,000 IP addresses, Leaseweb observed the following results:
- Nearly 98 percent of attacks were automatically mitigated through scrubbing
- Increased net promoter score (NPS), which translates to increased subscriber loyalty and stickiness
- A reduction in support tickets by about 11 percent
Click here to view the full case study.
Acorus Networks
Another case study comes from Acorus Networks, an internet service provider (ISP) based in France.
To defend against DDoS attacks, Acorus aimed to get as close to the attack source as possible.
Their criteria included:
- Secure connectivity IP transit
- HTTPS protection for API and websites
- Infrastructure protection
After deploying their DDoS scrubbing service, Acorus saw a variety of benefits, including:
- Full automation, without the need to scale their workforce to match the ever-increasing scale of DDoS attacks
- Unified management of hardware and virtual Thunder TPS appliances
- Effective deterrence of DDoS attacks
Summary
DDoS attacks continue to rise. For CSPs, implementing an automated DDoS mitigation solution in their network is a key step towards securing it.
After all, a CSP’s position in the network puts them in an ideal place to provide DDoS mitigation services to subscribers.
With a comprehensive, intelligent and automated DDoS scrubbing service in place, CSPs can meet both their and their subscribers’ individual needs, while still maintaining reliable performance and boosting profits.
On the other end of things, enterprises with a CSP that provides such DDoS scrubbing can enjoy greater visibility, uninterrupted service and customized security.
If their DDoS scrubbing service is implemented using the considerations mentioned above, all CSPs will find that those benefits will be well worth the investment.
This article is based off of a recent webinar by Don Shin of A10 Networks and Chief Analyst, Jim Hodges of Heavy Reading. Access the full webinar for free here.