IoT and DDoS: Cyberattacks on the Rise
The Internet of Things (IoT) may be a relatively new type of network, but it’s already seeing soaring adoption rates with no signs of stopping. In fact, IoT spending is expected to reach $267 billion by 2020.
However, IoT is not without its drawbacks: IoT devices are a common weapon in enormously destructive Distributed Denial of Service / DDoS attacks, and are predicted to be increasingly used as both attack targets and sources.
Here, we’ll take a closer look at the role of IoT in DDoS attacks.
How IoT Devices are Being Weaponized for a DDoS Attack
Partly because IoT is so new, it’s rife with insecurities. Due to of their lack of fundamental security controls, IoT devices are soft targets for cyber criminals and other aggressors. This means that they can be easily hacked and added to botnets, which are used to launch DDoS attacks against organizations.
In 2016, DDoS attacks on European web hosting company OVH and cybersecurity blog Krebs were traced back to IoT devices, including webcams, routers, digital video recorders and IP cameras.
In both cases, attackers successfully crippled the companies’ networks by hacking IoT devices protected by weak or hard-coded passwords, then incorporating those devices into the botnets which carried out the DDoS attacks. Neither attack was small, either the OVH attack maxed out at approximately 1 Tbps, and the DDoS attack on Krebs reached 620 Gbps.
Considering that IoT devices are used by countless companies across a wide array of industries, from trucking to insurance to communications, it isn’t necessarily surprising that IoT devices are being used by criminals to facilitate DDoS attacks.
Just some of the IoT devices used by businesses include:
- Cameras
- Sensors
- IoT cockpits
- Meters
- Thermostats
- Radio-frequency identification (RFID) tags
- Routers
While such devices can help to improve businesses’ efficiency, customer service and profit margin, as well as deliver valuable insights, they also come with significant security risks.
Gartner predicts that there will be more than 20 billion IoT devices in use by 2020, and when connected to a network, each one of those devices can act as an entry point for attackers.
Table: IoT Units Installed Base by Category (Millions of Units): Gartner (January 2017)
| Category | 2016 | 2017 | 2018 | 2020 |
|---|---|---|---|---|
| Consumer | 3,963.0 | 5,244.3 | 7,036.3 | 12,863.0 |
| Business: Cross-Industry | 1,102.1 | 1,501.0 | 2,132.6 | 4,381.4 |
| Business: Vertical-Specific | 1,316.6 | 1,635.4 | 2,027.7 | 3,171.0 |
| Grand Total | 6,381.8 | 8,380.6 | 11,196.6 | 20,415.4 |
For enterprises, some IoT devices pose greater risks than others, according to a report by ForeScout. The report, which was based on the research of a world-class ethical hacker, divided IoT devices into three categories of risk, from least to most severe: damaging, disruptive and disastrous.
- Damaging: Smart fridges and lightbulbs.
- Disruptive: VoIP phones, connected printers and smart video conference systems.
- Disastrous: IP-connected infrastructure (such as climate control and energy meters) and IP-connected security systems.
Additionally, with so many IoT devices generating such large amounts of data, it can be easy for malicious activity to go unnoticed.
Can Threat Intelligence Prevent Your IoT Devices from Being Hacked?
Zombies are very much real and walk amongst us (that is, in the form of compromised computers and devices).
Internet bots, also known as zombies, are computers or IoT devices that can be controlled by a third party thanks to the help of malicious apps or scripts. A group of zombies is called a botnet and is used by cybercriminals to launch DDoS attacks.
Once infected, botnets have been used time and again in DDoS attacks around the world, and their numbers are only increasing. They lurk in the shadows, connected to the internet and ready to spring into action at a moment’s notice.
What can companies use to defend themselves against botnets? In short, threat intelligence. As TechTarget puts it, “threat intelligence” is organized, analyzed and refined information about potential or current attacks that threaten an organization. This intelligence, when leveraged by an advanced and automated DDoS protection solution, can be used to identify weak spots and proactively strengthen DDoS defenses without wasting valuable time and resources.
The key word here is “automated.” Itâ’s simply impossible for any person, or even a large group of people, to identify all existing potential threats, let alone detect, understand and mitigate a DDoS attack once it’s underway. To illustrate this, let’s check out the A10 live threat intelligence map:
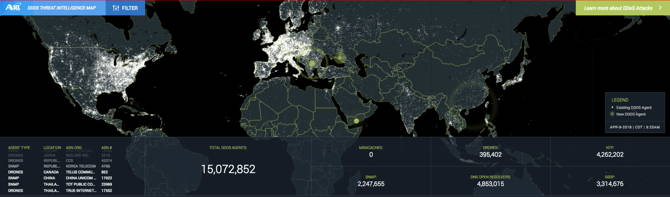
A10 DDoS Threat Intelligence Map
This map is a visualization of a live feed of A10 Networks’ threat intelligence. What you see is all the identified botnets lying in wait, ready to launch a DDoS attack within seconds.
It would take humans countless hours to collect such a vast amount of data, while an automated system can aggregate, categorize and analyze millions of data points in a fraction of the time. With that information, companies can protect themselves from zombies before they’re mobilized.
With more and more computers and insecure IoT devices being turned into zombies every day, it’s becoming increasingly clear that the next generation of DDoS protection requires a proactive, automated approach that’s based on comprehensive threat intelligence.
Takeaways
In order to protect networks from DDoS attacks, businesses must ensure that:
- Each connected IoT device adheres to stringent security protocols.
- The data each device generates is adequately encrypted.
- Algorithms and analytical tools are in place to identify malicious activity.
- Unauthorized devices are not permitted to access the network.
- An automated, threat intelligence-based approach is used.
With IoT DDoS attacks becoming larger and more frequent than ever, it’s essential that businesses recognize the many risks associated with IoT devices and work to mitigate them before they’re exploited.
Webinar
To learn more about IoT devices and how they factor in DDoS attacks, check out our webinar, “DDoS: Preparing for massive attacks and new regulations,” where we explain how forward-thinking enterprises are re-imagining their DDoS mitigation infrastructure.
Learn more information about A10’s DDoS mitigation and detection product.
Seeing is believing.
Schedule a live demo today.