HTTPS Interception and the Truth About Thunder SSLi Cipher Support
The A10 Networks Security Engineering Research Team recently reviewed the paper titled, “The Security Impact of HTTPS Interception,” which examines and grades the “security of TLS interception middleboxes,” including A10 Networks Thunder SSL Insight (SSLi).
Unfortunately, the authors of the report did not contact us for guidance on the appropriate configuration for their testing requirements. We have determined that the research ignored Guided mode (Wizard) configurations and focused only on Expert mode (CLI) configurations. The test requirements for this research paper could have been fully met with the correct configuration of our systems. We have reached out to the authors to voice our concerns, and are working with them to update their paper.
Here, we illustrate how the paper’s authors’ configurations were incomplete, which ultimately produced results that did not meet their requirements.
Before that, however, we’d be remiss not to note that research testing and examining security solutions is necessary to the industry, and we hope to see more in the future.
Advertising Ciphers
First, the grading notes indicate that A10 Thunder SSLi “advertises export ciphers.” Yes, ciphers in A10 Thunder SSLi can be advertised, but this only happens if an operator using the CLI chooses to enable all available ciphers. The operator can just as easily configure the system so that it does not advertise export ciphers.
For non-expert users, A10 Thunder SSLi offers wizard-based configuration tools, which are easy to follow and offer a smooth out-of-the-box experience. The wizard- and template-based configuration tools, which are currently available to all users, automatically apply best practices, which configures the system to not advertise export ciphers.
We believe that for their testing the paper’s authors configured the Thunder SSLi in the default configuration designed for experts and that they selected the “all available ciphers” setting, which is permissive to provide maximum coverage, but can be adjusted.
Modern Cipher Support
Which brings us to the second point. In the paper, the authors indicate that Thunder SSLi does not support “modern ciphers.” This is also false.
The system enables all modern ciphers, even in the default configuration. We believe the paper’s authors likely disabled all modern ciphers for the purpose of their study.
Here are some screenshots that show Thunder SSLi in operation and the built-in cipher suites. You can also see a sampling of the configuration templates:
SSLi Configuration Template
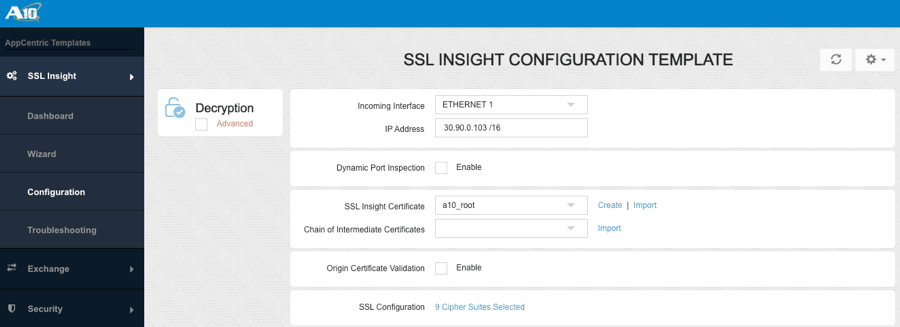
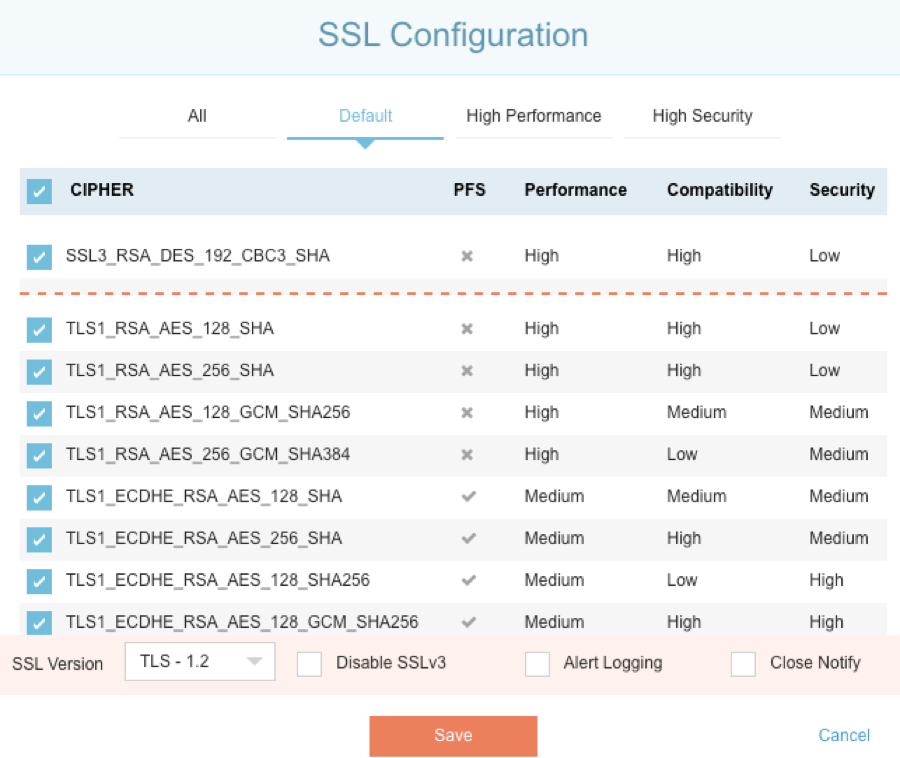
SSLi Default Cipher Configuration (Recommended For Non-Expert Users)
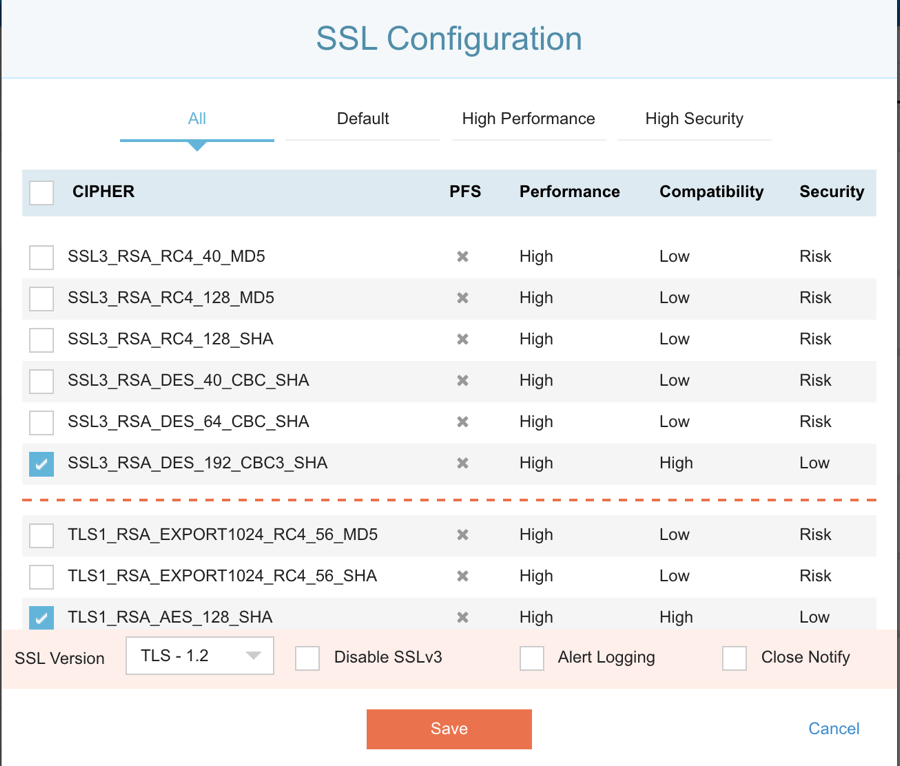
SSLi ‘All Cipher’ Configuration (For Expert Users)
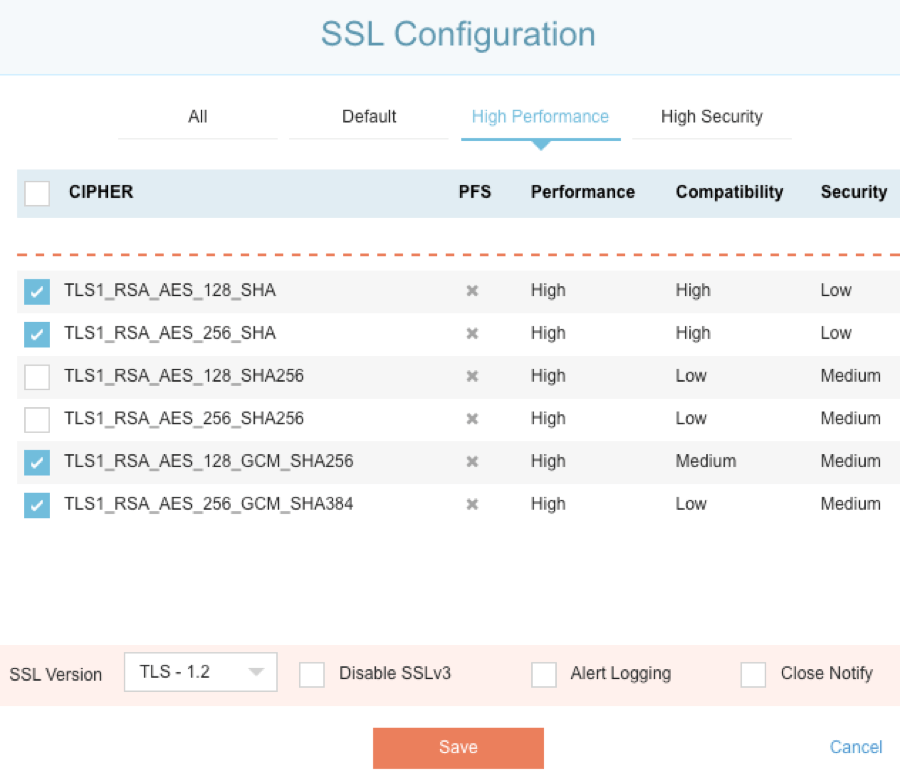
SSLi High-Performance Configuration
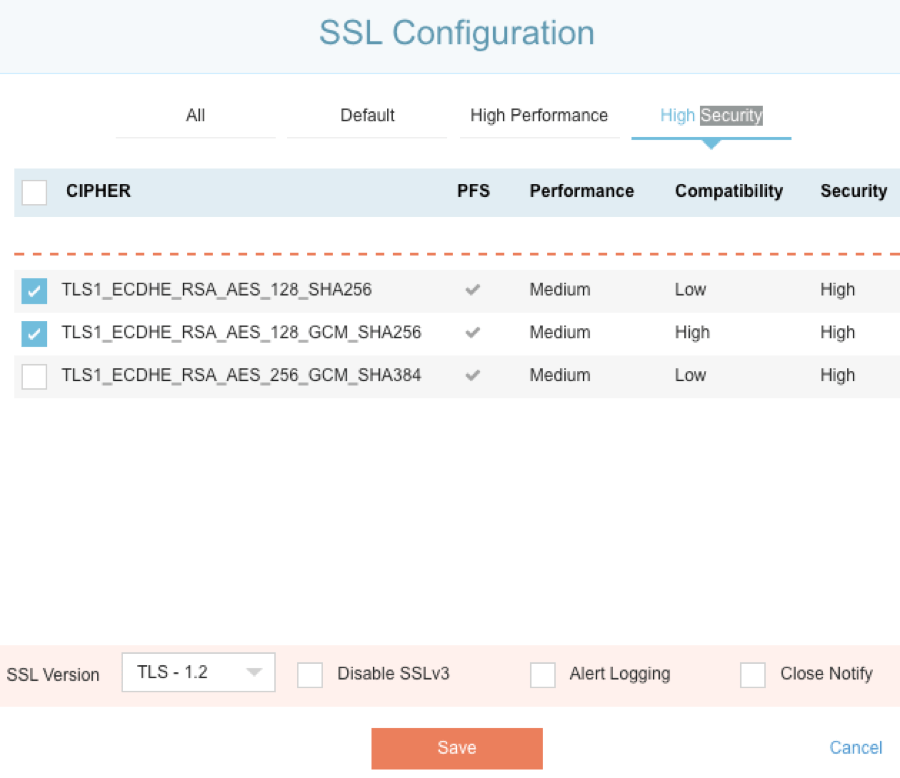
SSLi High-Security Configuration
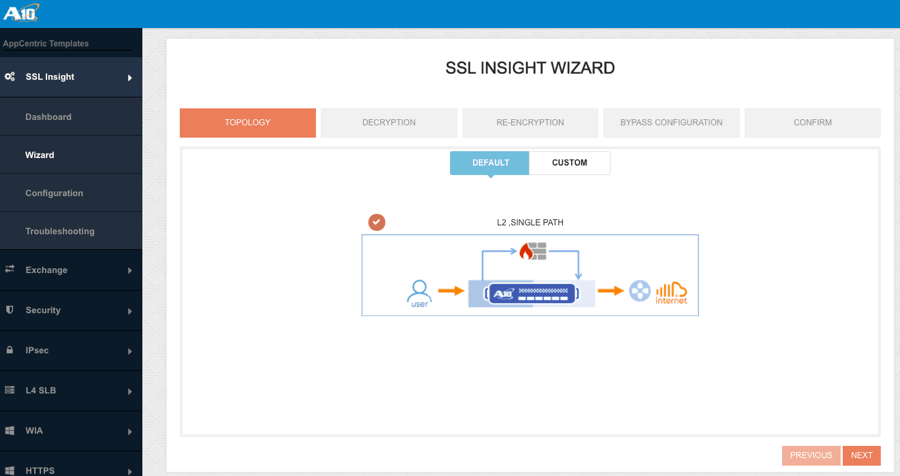
SSLi Configuration Wizard
While we don’t believe there was any malicious intent, the paper included inaccuracies and misinformation that were likely caused by lack of familiarity with our systems. We hope this clears up any questions you may have.
We’re excited to have an open dialogue with the paper’s authors and hope this sparks more accurate and thorough product testing, along with conversations about how the industry can improve cyber security.
For additional details on A10 Thunder SSLi, download this data sheet.
Seeing is believing.
Schedule a live demo today.