The State of DDoS Weapons, Q2 2019

A new version of the State of DDoS Weapons Report has been published. Learn more about the new report here.
(Archived)
DDoS attacks continue to grow in frequency, intensity and sophistication. However, the delivery method–using infected botnets and vulnerable servers to perform these attacks–remains the same. That said, we are seeing some new attack threats on the horizon in IoT and 5G. Read on to learn more.
Where DDoS Attacks Are Originating
Although DDoS weapons are globally distributed, you can find the highest concentration where internet-connected populations are denser.
Our research found the following to be the top seven countries hosting DDoS weapons:
- China
- USA
- Russia
- Italy
- Republic of Korea
- India
- Germany
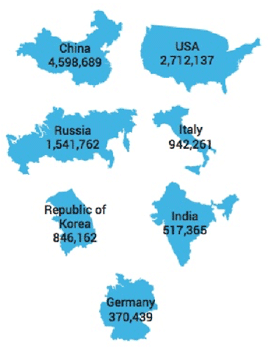
We tend to see the same countries competing for top spots in that list, though their position fluctuates. For example, in our Q4 2018 State of DDoS Weapons report, the top three were China, USA and Italy.
In our research from Q2 2019, we also found certain companies and government operators allowed large numbers of DDoS weapons (belonging to their users) to remain connected to their networks.
This allowed those users to carry out attacks on other networks and computers. Here are the top-five organizations allowing this to happen:
- China Unicom (China)
- China Telecom (China)
- TIM (Telecom Italia – Italy)
- Rostelecom (Russia)
- Korea Telecom (South Korea)
Mobile carriers are also hosting DDoS weapons. The top-five carriers according to our research included:
- Guangdong Mobile Communication Co. Ltd (China)
- Shandong Mobile Communication Company Ltd. (China)
- China Mobile Communications Corporation (China)
- T-Mobile (Czech Republic, the Netherlands, Poland and the United States)
- Henan Mobile Communications Co. Ltd (China)
According to the data, these are the top companies hosting DDoS botnet agents used to perform attacks:
- China Unicom
- Rostelecom
- China Telecom
- TE Data (Egypt)
- Baidu (Chinese multinational)
- DDoS Attacker Reconnaissance
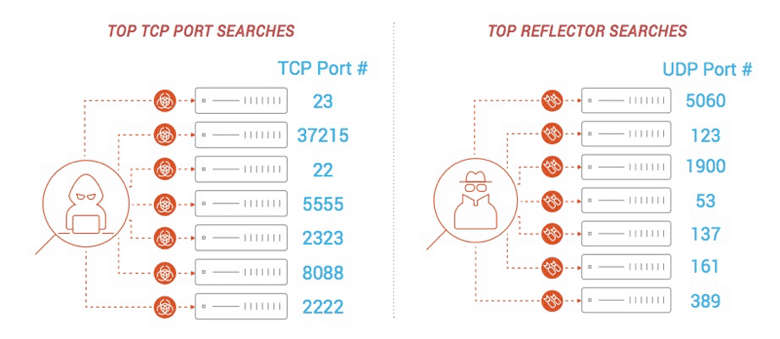
DDoS-for-hire bot herders scan and probe the internet for the following:
- Vulnerable IoT compute nodes through exposed TCP services
- Available amplified UDP services to continuously replenish their weapon stockpile
According to our latest research, the top TCP port searches include:
- 23
- 37215
- 22
- 5555
- 2323
- 8088
- 2222
Top reflector searches include UDP port numbers:
- 5060
- 123
- 1900
- 53
- 137
- 161
- 389
IoT: A Hotbed for DDoS Botnets
As we’ve written in the past, IoT devices and DDoS attacks are a perfect match.
With the explosion of the Internet of Things (growing at a rate of 127 connected devices per second and accelerating), attackers target vulnerable connected devices and have even begun to develop new strains of malware just for IoT.
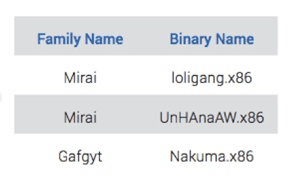
In our latest research, we highlighted the top-three IoT binary dropped by malware families–two of the three belong to Mirai.
And the top-five countries hosting malware droppers include:
- Netherlands
- UK
- USA
- Germany
- Russia
The New IoT Threat: COAP
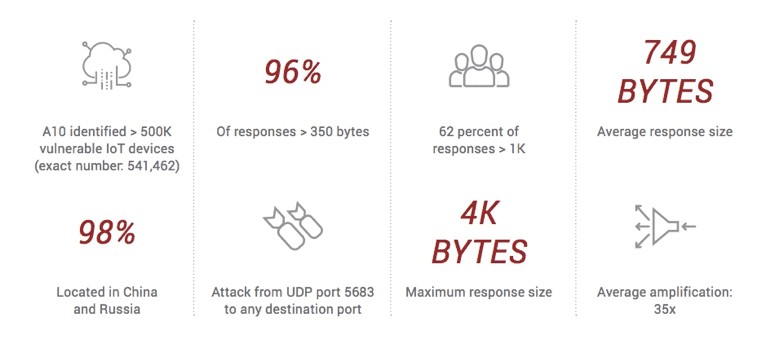
A new threat has emerged due to industry-wide adoption of technology with weak security: the UDP implementation of the Constrained Application Protocol (CoAP).
This has enabled millions of IoT devices to become weaponized as reflected amplification canons.
This machine-to-machine (M2M) management protocol is deployed on IoT devices supporting applications such as smart energy and building automation.
CoAP is a protocol implemented for both TCP and UDP and does not require authentication to reply with a large response to a small request.
Here’s a visual snapshot of the data we’ve collected on this new threat:
On the Horizon: 5G
5G will enable new IoT applications and use cases. It will also increase the DDoS weaponry available to attackers.
Ericsson recently predicted that the number of IoT devices with cellular connection will reach 4.1 billion by 2024.
These devices will not only increase in number, but also in speed. 5G, with its higher data speeds and lower network latency, will be the primary driver behind this rapid expansion.
Worth Noting: The Largest DDoS Attacks are Amplified
Amplified reflection attacks exploit the connectionless nature of the UDP protocol with spoofed requests to misconfigured open servers on the internet.
Attackers send volumes of small requests with the spoofed victim’s IP address to exposed servers, which are targeted because they’re configured with services that can amplify the attack.
These attacks have resulted in record-breaking volumetric attacks, such as the 1.3 Tbps Memcached-based GitHub attack in 2018, and account for the majority of DDoS attacks.
Every quarter, the findings of our DDoS attack research point to one thing: the need for increased security. DDoS attacks are not going away, and it’s time for organizations to match their attackers’ sophistication with a stronger defense, especially new technology like IoT and 5G gains momentum.
We update this report on a quarterly basis. For more information on the latest state of DDoS weaponry, download the “State of DDoS Weapons” report by A10 Networks.
Additional Resources
- Learn more about A10’s DDoS Protection solutions